Carrier-Grade NAT Configuration
Configuration Hierarchy
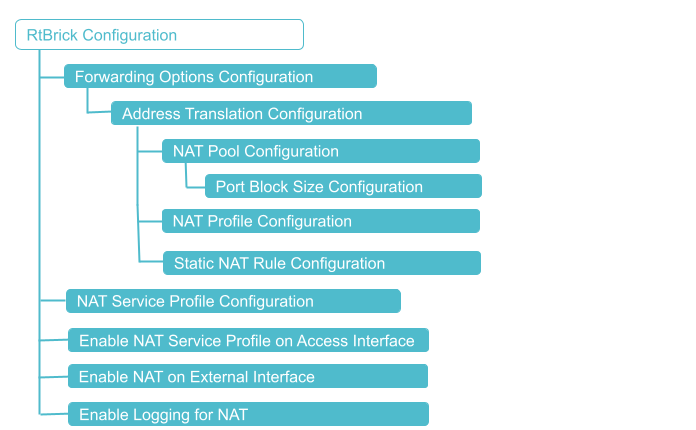
Prerequisites
Before configuring CGNAT, you must set the correct platform profile. Reboot the system for the changes to take effect, after setting the platform profile. For information about Platform Profile configuration, see Platform Profile.
CGNAT Configuration
You must perform the following tasks to configure CGNAT.
-
Configure NAT Pool
-
Configure NAT Profile
-
Configure NAT Rule
-
NAT Service Profile Configuration
-
Enable NAT on an Instance
-
Enable NAT Service Profile on Access Interface
-
Enable NAT on External Interface
-
Enable Logging for NAT
-
Enabling NAT ACL Support for ICMP and TCP Control Messages
Configuration Syntax and Commands
The following sections describe the CGNAT configuration syntax and commands.
Configuring NAT Profile
A NAT profile defines how the NAT device has to perform the IPv4 address translation. NAT profile allows you to define an instance, IPv4 address pools, maximum number of translations, and mapping a particular internal IPv4 address with a particular external IPv4 address for a deterministic address translation.
A single NAT profile can be attached to subscribers across different instances. This means that regardless of which instance a subscriber belongs to, they can share the same NAT profile. For example, subscribers in different routing instances can be managed using the same NAT settings.
Subscribers within the same instance can be assigned different NAT profiles. Different groups of subscribers or services within the same instance can have tailored NAT configurations.
| The configuration limit of NAT rules per subscriber in NAT profile is 16,384. |
Syntax:
| Attribute | Description |
|---|---|
|
Specify the NAT profile name. |
|
Specify deterministic as true to enable deterministic NAT for the profile. Deterministic NAT allows subscribers always to connect with a single public IP. |
|
Specify the protocol: tcp, udp, or other. |
|
Specify the ageing time value for the protocol. Default, 300 seconds for TCP and UDP. The allowed Ageing Time Out range values are as follows: |
|
Specify the TCP/UDP control plane ageing timeout value. The default values are as follows: TCP-control-plane: 10 seconds The allowed Ageing Time Out range values are as follows: TCP Control-plane: 5 - 120 |
|
Specify the maximum number of rules per subscriber or an interface. The supported values for maximum address translation per subscriber or an interface are 64, 128, 256, 512, 1024, 2048, 4096, 8192, and 16384. |
|
Specify the name of the public IP address pool. |
The following commands configure the NAT profile named nat_profile1. The nat profile nat_profile1 is configured on the instanced vrf1 with a pool attached nataddr_pool1. Maximum rules are configured as 128 rules and the aging period is configured as 600 seconds for TCP traffic, 300 seconds for UDP traffic, and 300 for 'other' traffic.
set forwarding-options address-translation profile nat_profile1 set forwarding-options address-translation profile nat_profile1 pool nataddr_pool1 set forwarding-options address-translation profile nat_profile1 max-rules 128 set forwarding-options address-translation profile nat_profile1 ip-protocol tcp ageing-timeout 600 set forwarding-options address-translation profile nat_profile1 ip-protocol udp ageing-timeout 300 set forwarding-options address-translation profile nat_profile1 ip-protocol other ageing-timeout 300
Example Configuration:
supervisor@rtbrick>cbng1.rtbrick.net: cfg> show config forwarding-options address-translation profile
{
"rtbrick-config:profile": [
{
"profile": "nat_profile1",
"pool": "nataddr_pool1",
"max-rules": "128",
"ip-protocol": {
"tcp": {
"ageing-timeout": 600
},
"udp": {
"ageing-timeout": 300
},
"other": {
"ageing-timeout": 300
}
}
}
]
}
NAT Pool Configuration
A NAT IP address pool includes a set of public IPv4 addresses that are used for network address translation. You can create multiple public IPv4 address pools and one pool includes a range of public IPv4 addresses. These pools allocate public IPv4 addresses to subscribers during address translation. While configuring a pool, you can define the group of public IPv4 addresses belonging to that pool by specifying the lowest and highest IP addresses.
The system allows you to create multiple pools and define the association among them. You can define the 'next-pool-name' that takes over when the current pool gets exhausted with the IPv4 addresses. When one pool gets exhausted, the next pool takes over and starts serving the IP addresses to subscribers when the address translation occurs.
| Static and dynamic IP pools cannot be configured simultaneously; they are mutually exclusive. |
Syntax:
| Attribute | Description |
|---|---|
|
Specify the name of the address pool. |
|
Specify both the highest and lowest IPv4 addresses in the range of IPv4 addresses for the pool. |
|
Specify the highest IPv4 address in the address pool. You must specify the highest IP address in the range of IP addresses. |
|
Specify the lowest IPv4 address in the address pool. You must specify the lowest IP address in the range of IP addresses. |
|
Specify the name of the next address pool that is to be used when the current address pool is allocated completely. |
Example Configuration:
The following commands configure nataddr_pool1 as the NAT pool and nataddr_pool2 as the next pool.
It indicates NAT pool nataddr_pool1 contains a range of public IPv4 addresses from 100.100.100.1 to 100.100.100.5.
When the pool nataddr_pool1 has fully allocated its IPv4 addresses, the next pool named nataddr_pool2 will start allocating IPv4 addresses from its pool. The pool nataddr_pool2 includes a rage of IPv4 address from 100.100.101.1 to 100.100.101.150.
set forwarding-options address-translation pool nataddr_pool1 set forwarding-options address-translation pool nataddr_pool1 next-pool-name nataddr_pool2 set forwarding-options address-translation pool nataddr_pool1 ipv4-address low 100.100.100.1 set forwarding-options address-translation pool nataddr_pool1 ipv4-address high 100.100.100.5 set forwarding-options address-translation pool nataddr_pool2 ipv4-address low 100.100.101.1 set forwarding-options address-translation pool nataddr_pool2 ipv4-address high 100.100.101.150
Example Configuration:
supervisor@rtbrick: cfg> show config forwarding-options address-translation pool
{
"rtbrick-config:pool": [
{
"pool-name": "nataddr_pool1",
"next-pool-name": "nataddr_pool2",
"ipv4-address": {
"low": "100.100.100.1",
"high": "100.100.100.5"
}
},
{
"pool-name": "nataddr_pool2",
"ipv4-address": {
"low": "100.100.101.1",
"high": "100.100.101.150"
}
}
]
}
NAT Rule Configuration
You can define NAT rules only for static NAT. A NAT rule defines a match condition and a corresponding action. After you specify NAT rules, each packet is matched with each NAT rule. If a packet matches the condition specified in a rule, then the action corresponding to that match occurs. Match rules govern how the translation of private IPv4 addresses to public IPv4 addresses is performed.
With NAT rules, you can define how address translation is applied to traffic, and how to handle various protocols and data traffic, such as TCP and UDP, to ensure proper address translation and the mappings of private addresses to public addresses.
Rules also define how to handle inbound and outbound traffic, different protocols, and data traffic such as TCP and UDP for ensuring the proper address translation of traffic.
| Configuration limit for NAT maximum rules per subscriber is 16,384. |
Syntax:
| Attribute | Description |
|---|---|
|
Specify the name of the rule. |
|
Specify the ordinal value. An ordinal value is a numerical representation that indicates its relative position or order. |
|
Specify the RBFS instance name. |
|
Specify the IP protocol, TCP or UDP. |
|
Specify the private IPv4 address or port number that needs to be translated. |
|
Specify the public IPv4 address. This public IP will be mapped with the private IP in the translation table. |
Configuring NAT Service Profile
You must create a NAT service profile and attach the service profile with the access interface for enabling CGNAT on the interface.
Syntax:
| Attribute | Description |
|---|---|
|
Name of the service profile. |
|
Specify the profile name for the address translation. |
The following configuration defines a service profile named nat_service. It associates the NAT profile named 'nat_profile1' to the 'nat_service' profile. It indicates any subscriber using this service profile will use the configuration defined in nat_profile1.
set access service-profile nat_service set access service-profile nat_service address-translation profile nat_profile1
Example:
{
"rtbrick-config:service-profile": [
{
"profile-name": "nat_service",
"address-translation": {
"profile": "nat_profile1"
},
"qos": {
"profile": "subs-triple-play"
}
}
]
}
Enable NAT Service Profile on the Access Interface
It is required to attach the NAT service profile to the access interface for enabling address translation on the interface.
Syntax:
| Attribute | Description |
|---|---|
|
Configure global service profile. |
|
Specify the minimum number of outer VLANs. Allowed range: 1 - 4094. |
|
Specify the maximum number of outer VLANs. Allowed range 1 - 4094. |
|
Specify the minimum number of inner VLANs. Allowed range: 1 - 4094. |
|
Specify the maximum number of inner VLANs. Allowed range 1 - 4094. |
|
Specify the name of the service profile. |
The following commands attach service profile nat_service to the interface (double-tagged) ifp-0/0/17. The configuration shows the range of outer VLANs as 1000 - 1007, and the range inner VLANs as 84 - 4084. The access type configured is IPoE and the service profile is NAT service. AAA profile name is ipoe-aaa and the gateway IFL is lo-0/0/0/100.
IPoE subscriber with outer VLAN between 1000 and 1007, and inner VLAN between 84 and 4084 will be matched with this NAT service profile and a corresponding action will be taken. Anything outside these vlans will not have any action from this NAT service profile.
set access interface double-tagged ifp-0/0/17 1000 1007 84 4084 set access interface double-tagged ifp-0/0/17 1000 1007 84 4084 access-type IPoE set access interface double-tagged ifp-0/0/17 1000 1007 84 4084 access-profile-name ipoe set access interface double-tagged ifp-0/0/17 1000 1007 84 4084 service-profile-name nat_service set access interface double-tagged ifp-0/0/17 1000 1007 84 4084 aaa-profile-name ipoe-aaa set access interface double-tagged ifp-0/0/17 1000 1007 84 4084 gateway-ifl lo-0/0/0/100
{
"rtbrick-config:interface": {
"double-tagged": [
{
"interface-name": "ifp-0/0/17",
"outer-vlan-min": 1000,
"outer-vlan-max": 1007,
"inner-vlan-min": 84,
"inner-vlan-max": 4084,
"access-type": "IPoE",
"access-profile-name": "ipoe",
"service-profile-name": "nat_service",
"aaa-profile-name": "ipoe-aaa",
"gateway-ifl": "lo-0/0/0/100"
}
]
}
}
The following commands configure a double-tagged interface ifp-0/0/6 and outer VLAN minimum value is 1000, maximum value as 1007, inner VLAN minimum value as 84 and maximum value as 4084. The access type configured is PPPoE, service profile is NAT service. AAA profile name is configured as ipoe-aaa.
It indicates PPPoE subscriber with outer VLAN between 1000 and 1007, and inner VLAN between 84 and 4084 will be matched with this NAT service profile and a corresponding action will be taken. Anything outside these vlans will not have any action from this NAT service profile.
set access interface double-tagged ifp-0/0/16 1000 1007 84 4084 set access interface double-tagged ifp-0/0/16 1000 1007 84 4084 access-type PPPoE set access interface double-tagged ifp-0/0/16 1000 1007 84 4084 access-profile-name pppoe set access interface double-tagged ifp-0/0/16 1000 1007 84 4084 service-profile-name nat_service set access interface double-tagged ifp-0/0/16 1000 1007 84 4084 aaa-profile-name ipoe-aaa
Example:
{
"rtbrick-config:interface": {
"double-tagged": [
{
"interface-name": "ifp-0/0/16",
"outer-vlan-min": 1000,
"outer-vlan-max": 1007,
"inner-vlan-min": 84,
"inner-vlan-max": 4084,
"access-type": "PPPoE",
"access-profile-name": "pppoe",
"service-profile-name": "nat_service",
"aaa-profile-name": "ipoe-aaa"
},
]
}
}
Enable NAT on an Instance
You can enable address translation for a specific routing instance such as VRF or virtual router rather than globally across the entire router.
Syntax:
| Attribute | Description |
|---|---|
|
Name of the instance. |
The following command is used to enable address translation for the instance named 'vrf1'.
set instance vrf1 address-translation true
supervisor@rtbrick.net: op> show config instance vrf1 address-translation
{
"rtbrick-config:address-translation": "true"
}
Enable NAT on External Interface
It is required to enable the NAT on the external (core-facing) interface.
Syntax:
| Attribute | Description |
|---|---|
|
Name of the interface. |
|
Configure the number of sub-interfaces under the physical interface. |
|
Specify 'public' for the external interface. |
The following commands configure the external interface ifp-0/1/64 for IPv4 address translation. 'Unit' logical identifier for this physical interface. Direction 'public' shows the configuration on external interface for address translation.
set interface ifp-0/1/64 unit 100 set interface ifp-0/1/64 unit 100 address-translation set interface ifp-0/1/64 unit 100 address-translation direction public
supervisor@rtbrick.net: cfg> show config interface ifp-0/1/64 unit 100
{
"rtbrick-config:unit": [
{
"unit-id": 100,
"address-translation": {
"direction": "public"
}
}
]
}
Enable Logging for NAT
You can optionally enable logging for CGNAT operations.
| All RBFS logs and related information is available in the RBFS Logging User Guide. For the list of RBFS logs, see Log Reference. |
| Attribute | Description |
|---|---|
|
Specify the log level. |
|
Specify the log module. |
|
Specify the plugin-alias URL. Plugin-alias is an external logging host server to which you can export logs. For example, Graylog. |
The following commands configure logging for NAT module natd with a log level 'debug'.
set log bd natd set log bd natd module nat set log bd natd module nat level debug
supervisor@rtbrick.net: cfg> show config log bd natd
{
"rtbrick-config:bd": [
{
"bd-name": "natd",
"module": [
{
"module-name": "nat",
"level": "debug"
}
]
}
]
}
Enabling NAT ACL Support for ICMP and TCP Control Messages
You can enable Access Control Lists support for ICMP and TCP Control messages.
Enabling NAT Support for ICMP Using ACLs
The NAT ACLs for ICMP packets allows address translation for ICMP request and response packets through the use of Access Control Lists (ACLs). This enhances the handling of ICMP traffic by providing precise control over NAT behavior for ICMP packets.
| Setting up the NAT ACLs for ICMP will be handled by the NAT application with the 25.1.1 release, eliminating the need for manual configuration. |
| Attribute | Description |
|---|---|
|
Specify the name of the rule. |
|
Specify the ordinal value. An ordinal value is a numerical representation that indicates its relative position or order. |
|
Define the conditions under which the rule will be applied. These conditions determine which packets the rule should act on. |
|
Defines what happens to packets that match the rule’s criteria. |
|
Determines the priority of the rule when multiple rules with the same ordinal value are evaluated. |
|
The rule applies to ingress or egress traffic. |
Example commands:
set forwarding-options acl l3v4 rule NAT_TRAP set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1001 set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1001 match direction ingress set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1001 match ip-protocol icmp set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1001 match destination-ipv4-prefix-list PREFIXES_NAT_PUBLIC set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1001 action trap nat set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1001 priority 1001 set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1002 set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1002 match direction ingress set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1002 match source-ipv4-prefix 100.64.0.0/10 set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1002 match ip-protocol icmp set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1002 action trap nat set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1002 priority 1002
Example:
supervisor@rtbrick.net: cfg> show config forwarding-options acl l3v4
{
"rtbrick-config:l3v4": {
"rule": [
{
"rule-name": "NAT_TRAP",
"ordinal": [
{
"ordinal-value": 1001,
"match": {
"direction": "ingress",
"ip-protocol": "icmp",
"destination-ipv4-prefix-list": "PREFIXES_NAT_PUBLIC"
},
"action": {
"trap": "nat"
},
"priority": 1001
},
{
"ordinal-value": 1002,
"match": {
"direction": "ingress",
"source-ipv4-prefix": "100.64.0.0/10",
"ip-protocol": "icmp"
},
"action": {
"trap": "nat"
},
"priority": 1002
}
]
}
]
}
}
The preceding configuration defines Layer 3 IPv4 Access Control List (ACL) rules for managing ICMP traffic. The rule with the ordinal value 1001 is designed to redirect ICMP traffic for Network Address Translation (NAT) processing based on specific criteria. The ACL rule is named NAT_TRAP.
The matching criteria for this rule include the direction of traffic, which is set to ingress. This means the rule applies only to incoming traffic. The specified protocol is ICMP, indicating that the rule is applicable to ICMP packets.
The 'destination-ipv4-prefix-list' is designated as PREFIXES_NAT_PUBLIC, which is a predefined list containing a range of IPv4 addresses. The rule specifically pertains to ICMP packets whose destination IP is included in the PREFIXES_NAT_PUBLIC list. These rules ensure that ICMP packets requiring NAT handling are identified and appropriately redirected to the NAT process. When an ICMP packet that meets the conditions (ingress, ICMP, and a destination in PREFIXES_NAT_PUBLIC) is detected, it is redirected (or punted) to the NAT process for further handling.
Enabling NAT Support for TCP Control Messages Using ACL
This configuration enables address translation on TCP control messages through ACLs. The feature supports control messages such as FIN, SYN, and RST. It applies functionality to TCP control messages such as fin-ack and rst-ack.
| Setting up the NAT ACLs for TCP control messages will be handled by the NAT application with the 25.1.1 release, eliminating the need for manual configuration. |
Syntax:
| Attribute | Description |
|---|---|
|
Specify the name of the rule. |
|
Specify the ordinal value. An ordinal value is a numerical representation that indicates its relative position or order. |
|
Define the conditions under which the rule will be applied. These conditions determine which packets the rule should act on. |
|
Defines what happens to packets that match the rule’s criteria. |
|
Determines the priority of the rule when multiple rules with the same ordinal value are evaluated. |
|
The rule applies to ingress or egress traffic. |
|
Matches TCP packets with the FIN-ACK control flag set. Note: When using the tcp-control match attribute in a match rule, it is necessary to explicitly configure match ip-protocol for TCP. This ensures that the rule accurately identifies and processes TCP packets before applying any matching for TCP control flags. |
|
Name of the prefix list. The list includes predefined destination IP addresses. |
Example commands:
set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1003 set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1003 match direction ingress set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1003 match tcp-control fin-ack set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1003 match destination-ipv4-prefix-list PREFIXES_NAT_PUBLIC set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1003 action trap nat set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1003 priority 1003 set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1004 set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1004 match direction ingress set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1004 match source-ipv4-prefix 100.64.0.0/10 set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1004 match tcp-control fin-ack set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1004 action trap nat set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1004 priority 1004 set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1005 set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1005 match direction ingress set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1005 match tcp-control rst-ack set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1005 match destination-ipv4-prefix-list PREFIXES_NAT_PUBLIC set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1005 action trap nat set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1005 priority 1005 set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1006 set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1006 match direction ingress set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1006 match source-ipv4-prefix 100.64.0.0/10 set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1006 match tcp-control rst-ack set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1006 action trap nat set forwarding-options acl l3v4 rule NAT_TRAP ordinal 1006 priority 1006
Example:
supervisor@rtbrick.net: cfg> show config forwarding-options acl l3v4
{
"rtbrick-config:l3v4": {
"rule": [
{
"rule-name": "NAT_TRAP",
"ordinal": [
{
"ordinal-value": 1003,
"match": {
"direction": "ingress",
"tcp-control": "fin-ack",
"destination-ipv4-prefix-list": "PREFIXES_NAT_PUBLIC"
},
"action": {
"trap": "nat"
},
"priority": 1003
},
{
"ordinal-value": 1004,
"match": {
"direction": "ingress",
"source-ipv4-prefix": "100.64.0.0/10",
"tcp-control": "fin-ack"
},
"action": {
"trap": "nat"
},
"priority": 1004
},
{
"ordinal-value": 1005,
"match": {
"direction": "ingress",
"tcp-control": "rst-ack",
"destination-ipv4-prefix-list": "PREFIXES_NAT_PUBLIC"
},
"action": {
"trap": "nat"
},
"priority": 1005
},
{
"ordinal-value": 1006,
"match": {
"direction": "ingress",
"source-ipv4-prefix": "100.64.0.0/10",
"tcp-control": "rst-ack"
},
"action": {
"trap": "nat"
},
"priority": 1006
}
]
}
]
}
}
The preceding configuration defines ACL for Layer 3 IPv4 traffic. The ACL is named NAT_TRAP and consists of multiple rules that match specific traffic patterns and apply a 'trap' action to punt the traffic for further NAT processing. Each rule is identified by an ordinal value.
Match Criteria includes direction which is specified as ingress. All rules are applied to ingress traffic. Protocol is defined as TCP traffic with specific control flags: fin-ack, rst-ack, and rst.
In the configuration:
-
Ordinal 1003 matches TCP traffic with the
fin-ackflag and a destination IP in the PREFIXES_NAT_PUBLIC list. -
Ordinal 1004 matches TCP traffic with the
fin-ackflag and a source IP in the 100.64.0.0/10 range. -
Ordinal 1005 matches TCP traffic with the
rst-ackflag and a destination IP in the PREFIXES_NAT_PUBLIC list. -
Ordinal 1006 matches TCP traffic with the
rst-ackflag and a source IP in the 100.64.0.0/10 range.
Modifying the Policer on NAT Trap
You can modify a 'policer' associated with NAT traps, which directs certain packets to the control plane (hostpath). A NAT trap indicates when a device is performing network address translation, some packets that require special handling, are diverted to the control plane for processing.
To change the policer for NAT traps, use the following command:
Syntax:
| Attribute | Description |
|---|---|
|
Specify the name of the policer. |
Example for modifying the policer for NAT trap.
set forwarding-options address-translation trap policer _DEFAULT_POLICER_5_MB