Lawful Interception Overview
Lawful Interception (LI) is a legal requirement mandated by national regulations in many regions. It enables authorized Law Enforcement Agencies (LEA) to access specific communication data from Communication Service Providers (CSP).
In RBFS, Lawful Interception enables the selective capture of subscriber sessions in both directions (upstream and downstream). The intercepted traffic is tunneled to a Mediation Device (MD), along with metadata indicating the direction of capture and a reference to the intercepted connection or session.
RBFS supports LI in accordance with applicable technical standards and regulatory requirements. The system enables dynamic rule provisioning and role-based access control, ensuring that only authorized personnel can configure or view LI-related information. All interception activities can be logged for auditing and compliance purposes.
Components of Lawful Interception
The figure below shows the different components of the LI solution.
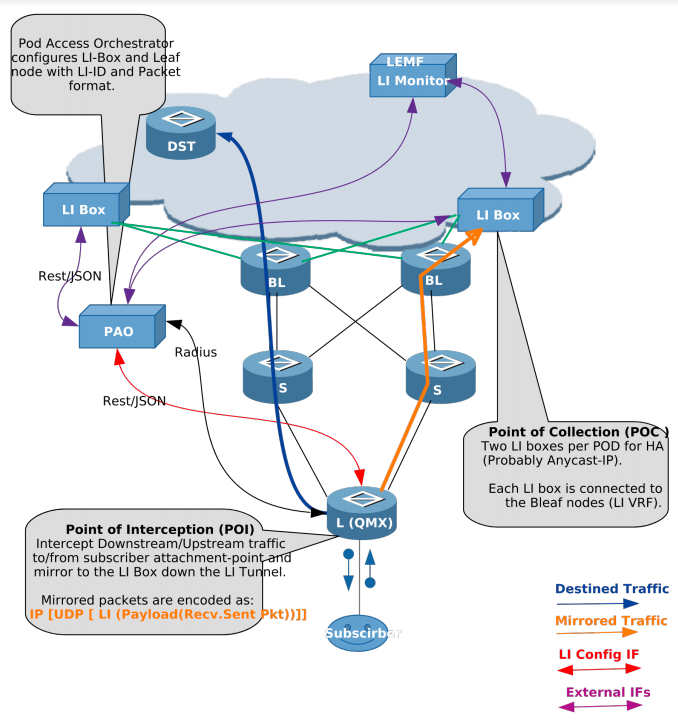
RBFS supports multiple integration methods to implement Lawful Interception (LI), providing flexibility to match the operator’s legal and technical requirements. The following three interfaces are supported for provisioning and managing interception sessions:
-
ETSI X1 Interface (see ETSI TS 101 671)
-
RADIUS Access-Accept and CoA using encrypted attributes
-
HTTP (REST) API
All three methods allow RBFS to set up interception sessions with precise control over subscriber identification, traffic direction, and metadata enrichment. Intercepted traffic is then tunneled to a Mediation Device (MD) using protocols compliant with national regulatory requirements. Role-based access control and full logging ensure that all LI-related actions are secure, traceable, and compliant.
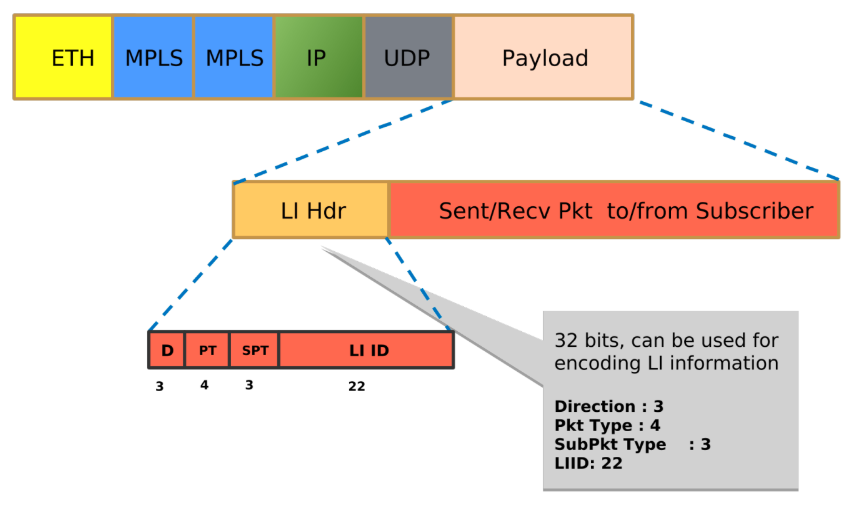
Packet Format Encoding for LI Headers
Packet Format Encoding describes the structure of the Lawful Interception (LI) header, which is a 32-bit construct.. This comprises four distinct fields: 3 bits for Direction, 4 bits for Packet type, 3 bits for Sub-Packet type, and 22 bits for LI ID. Each field serves a specific purpose in data transmission.
-
Direction (3 bits): Indicates the flow of data.
-
Packet type (4 bits): Specifies the kind of packet being transmitted.
-
Sub-Packet type (3 bits): Provides a more granular classification within a given packet type.
-
LI ID (22 bits): An identifier for the LI header itself.
Payload Direction:
Payload Direction indicates the flow of data and has the following values:
| Value | Payload Direction |
|---|---|
1 |
Reserved for keepalive mechanism |
2 |
Intercepted data or event was sent to target (downstream) |
3 |
Intercepted data or event was sent from target (upstream) |
Mapping Payload Format:
Mapping Payload Format has the following values:
| Value | Payload Format |
|---|---|
0-3 |
Reserved (unused) |
4 |
Unknown, Not able to decide the PT |
5 |
IPv4 packet (not used) |
6 |
IPv6 packet (not used) |
7 |
Ethernet Frame (used for Lawful Interception) |
Sub-payload Format (Type):
The sub-payload formats are used in the context of Lawful Interception (LI) to classify and manage intercepted data. These formats help in providing a more granular classification within a given packet type.
The sub-payload formats are:
-
Single VLAN tag
-
Double VLAN tag
-
Untagged
Supported Platforms
Feature availability may vary between hardware platforms. Refer to the Platform Guide for detailed information on which features and sub-features are supported on each specific platform.