BGP-signaled L2VPN Overview
The BGP-signaled L2VPN uses BGP for signaling and auto-discovery to establish multipoint Layer 2 VPN over the MPLS backbone network. The remote cross-connect is a point-to-point (P2P) service that connects two locations using the MPLS core network and MP-BGP. The remote cross-connect uses MPLS tunnels to traverse the backbone network. It offers a Layer 2 packet forwarding mode that connects access circuits (ACs). The RBFS implementation of BGP-signaled L2VPN is in accordance with RFC-6624 which supports L2VPN using BGP for auto-discovery and Signaling.
Supported Standards
| RFC Number | Description |
|---|---|
6624 |
Layer 2 Virtual Private Networks Using BGP for Auto-Discovery and Signaling |
BGP-signaled L2VPN Network Model
As shown in the figure below, a BGP-signaled L2VPN network contains the following building blocks:
-
Customer edge (CE)—Customer device directly connected to the service provider network.
-
Provider edge (PE)—Service provider device connected to CEs. PEs provide access to the Pseudowire network and forward traffic between customer network sites by using public tunnels.
-
Attachment circuit (AC)—A physical or virtual link between a CE and a PE.
-
Pseudowire (PW)—A virtual bidirectional connection between two PEs. A PW comprises a pair of virtual links in opposite directions.
-
MPLS transport tunnel—A connection that carries one or more PWs across the MPLS core or IP backbone, such as an MPLS tunnel.
-
Cross-connect—A connection formed by two physical or virtual circuits, such as ACs and PWs, that switches packets between them.
The figure below shows the protocol packet exchange process in the BGP-signaled L2VPN.
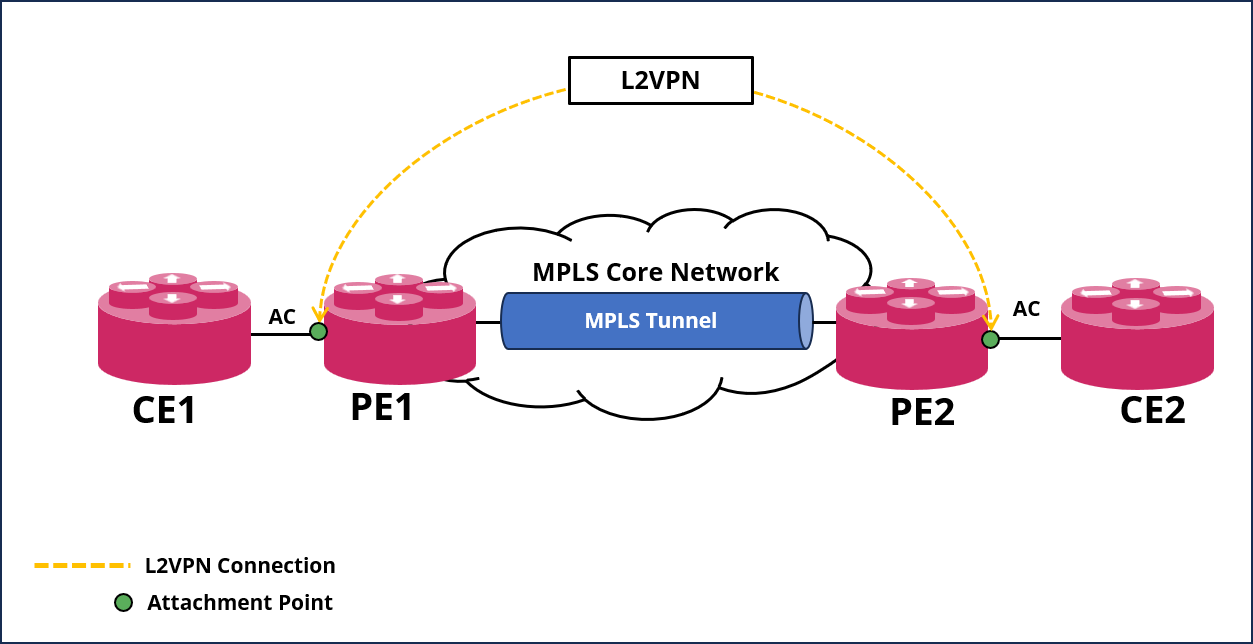
PE1 and PE2 are each configured with a BGP L2VPN instance. After the PE receives packets from the AC, it adds the PW label and sends them to the peer PE through the MPLS transport tunnel. After the other PE receives the packet via the MPLS transport path, it removes the PW label of the packets and forwards the packets to the AC bound to the PW.
VLAN Tag Manipulation
VLAN Tag Manipulation involve modifying VLAN tags on Ethernet frames to ensure proper traffic segmentation and delivery across a Layer 2 network. RBFS supports some VLAN Tag Manipulation operations which are used to manipulate tags on Ethernet frames as they enter or leave a network interface. These manipulations include adding, removing, and rewriting VLAN tags. VLAN manipulation operations can be performed both at ingress and egress nodes.
The following VLAN manipulation operations are supported for Layer 2 VPN interfaces:
-
push: Adds a single outer VLAN tag to an Ethernet frame.
-
pop: Removes a single outer VLAN tag from an Ethernet tag frame.
-
swap: Rewrite a single outer VLAN tag of an Ethernet tag frame.
-
push–push: Adds two VLAN tags to an Ethernet frame.
-
pop-pop: Removes two VLAN tags from an Ethernet tags frame.
-
swap–swap: Rewrite both the outer and inner VLAN tags of an Ethernet tags frame.
-
swap–push: Rewrite the outer VLAN tag and add a new inner VLAN tag for Ethernet tags' frame.
-
pop–swap: Removes the outer VLAN tag and rewrites the inner VLAN tag of an Ethernet tags' frame.
Supported CLI Options for VLAN Tag Manipulation Operations
The following table presents the various VLAN tag manipulation operations and supported CLI options.
| CLI Options | pop | push | swap | push-push | pop-pop | swap-push | swap-swap | pop- swap |
|---|---|---|---|---|---|---|---|---|
vlan-id |
No |
Yes |
Yes |
Yes |
No |
Yes |
Yes |
Yes |
vlan-encapsulation |
No |
Yes |
Yes |
Yes |
No |
Yes |
Yes |
Yes |
innervlan-id |
No |
No |
No |
Yes |
No |
Yes |
Yes |
No |
Supported Platforms
Not all features are necessarily supported on each hardware platform. Refer to the Platform Guide for the features and the sub-features that are or are not supported by each platform.