Policy Configuration
Configuration Hierarchy
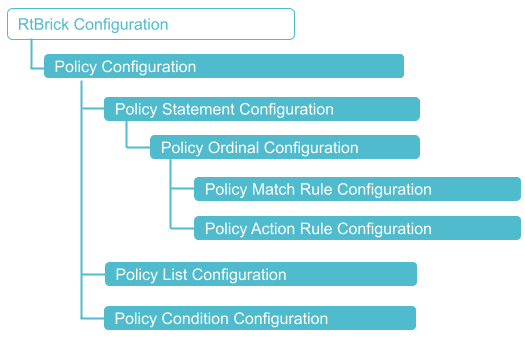
The diagram illustrates the policy configuration hierarchy.
Configuration Syntax and Commands
The following sections describe the policy configuration syntax and commands.
Configuring Policy Statements
Syntax:
| Attribute | Description |
|---|---|
|
Name of the policy statement. Policy names can contain alphanumeric characters and underscore character. They must not include special characters like hyphen. For example, BGP-EXPORT is not supported, whereas BGP_EXPORT is supported. A valid name cannot start with a number but it can contain numbers and underscore in the string. The length of the names should not exceed 64 characters. |
|
Specifies the ordinal number. |
|
Description of the ordinal. |
|
Match configuration hierarchy. Refer to the Configuring Match Rules section for details on the match rule configuration. |
match-logic <value> |
Specifies the match logic. Supported values are |
|
Action configuration hierarchy. Refer to the Action Rule Configuration section for details on the action rule configuration. |
|
Optionally, apply a policy condition. Refer to the Configuring Policy Conditions for the policy condition configuration. |
Configuring Match Rules
Syntax:
| Attribute | Description | ||
|---|---|---|---|
|
Specifies the match rule number. |
||
|
Specifies the attribute type. Refer to the Attribute and Match Types section for details on the supported attribute types. |
||
|
Specifies the match type. Refer to the Attribute and Match Types section for details on the supported match types per attribute, and to the Match Types section for descriptions of the match types. |
||
|
Attribute value. This is the actual value of the attribute to match, for example an IP prefix, a metric, or a community. |
||
|
Attribute value2.
|
||
|
Attribute value type. |
Attribute and Match Types
| Attribute Type | Match Types Supported |
|---|---|
|
regex |
|
regex |
|
regex |
|
regex |
|
exact |
|
exact |
|
regex |
|
regex |
|
regex |
|
regex |
|
regex |
|
regex |
|
regex |
|
regex |
|
regex |
|
regex |
|
regex |
|
regex |
|
exact |
|
regex |
|
regex |
|
regex |
|
regex |
|
regex |
|
regex |
|
regex |
|
exact |
|
regex |
|
regex |
|
exact |
|
regex |
|
regex |
|
regex |
|
regex |
|
regex |
Match Types
| Match Types | Description |
|---|---|
|
An attribute can be matched using a standard Linux egrep regular expression. Example: "label": "label-op:push,label:206,bos:1" In this example, the label is a 64bit number, which has label value, bos, and operation encoding. A |
|
Value configured in the command must be same as application attribute value |
|
This is applicable only for array type attribute; an exist match is the one where value configured in the command must exist in the application attribute value which is an array. |
|
The application attribute value must be less than the value configured in the command |
|
The application attribute value must be less than or exact value configured in the command |
|
The application attribute value must be greater than the value configured in the command |
|
The application attribute value must be greater than or exact value configured in the command |
|
The route shares the same most-significant bits (described by prefix-length), and prefix-length is greater than the route’s prefix length |
|
The route shares the same most-significant bits (described by prefix-length), and prefix-length is equal to or greater than the route’s prefix length. |
|
The route address shares the same most-significant bits as the match prefix (destination-prefix or source-prefix). The number of significant bits is described by the prefix-length component of the match prefix. The match will be performed only for prefixes longer than the one supplied for matching. |
|
The route address shares the same most-significant bits as the match prefix (destination-prefix or the source-prefix). The number of significant bits is described by the prefix-length component of the match prefix. The match is performed for the prefix supplied and for any prefixes that are subnets of it. |
|
The "neighbor" match-type specifically targets the AS number of the neighboring peer in the RIB entry. |
|
The "transit" match-type matches for AS numbers in rib-entry excluding neighbor and origin. |
|
The "origin" match-type matches for origin as-path number. |
|
The application attribute value whose prefix length must be lesser than or exact the value configured in the command |
|
The application attribute value whose prefix length must be greater than the value configured in the command |
|
The application attribute value whose prefix length must be greater than or exact value configured in the command |
Well-known Communities Regex Match
You must specify the value differently to match well-known communities using regex. For example, you can use the following regex pattern to match well-known communities: NO_EXPORT, NO_ADVERTISE, NO_EXPORT_SUBCONFED, and NOOPER.
This pattern works as follows:
NO* matches any string that starts with NO.
This will successfully match the following well-known communities because they start with NO.
-
NO_EXPORT
-
NO_ADVERTISE
-
"NO_EXPORT_SUBCONFED"
-
"NOPEER"
Configuring Action Rules
Syntax:
| Attribute | Description |
|---|---|
|
Specifies the action rule number. |
|
Specifies the operation type. Refer to Operation Types section for details on the supported operations, and to the Attribute Types and Supported Operations section for details on the operations per attribute. |
|
Specifies the attribute type. Refer to section Attribute Types and Supported Operations section for details on the supported attribute types. |
|
Specifies the operation value. |
Operation Types
| Operation Type | Description |
|---|---|
|
The application attribute value will be added with the value configured in the command |
|
The application attribute value will be appended with the value configured in the command |
|
Deletes the attribute from the route. It clears all the information for that specific attribute in the object. |
|
Deletes the specific value of an attribute from the route. It is mandatory to define match rules, before configuring the |
|
The application attribute value will be divided with the value configured in the command |
|
(Optional). By default, continue with the next policy in the policy chain. |
|
The application attribute value will be multiplied with the value configured in the command |
|
The application attribute value will be overwritten with the value configured in the command |
|
The application attribute value will be prefixed with the value configured in the command |
|
Stops policy execution and returns result as |
|
Stops policy execution and return result as permit (resulting route/BDS object to be permitted) |
|
The application attribute value will be subtracted with the value configured in the command. If the result of the subtraction results in a number less than 0, the value "0" is used. |
Attribute Types and Supported Operations
| Attribute Type | Operation Types Supported |
|---|---|
|
append |
|
append |
|
append |
|
append |
|
overwrite |
|
overwrite |
|
overwrite |
|
add |
|
overwrite |
|
overwrite |
|
overwrite |
|
overwrite |
|
overwrite |
|
overwrite |
|
overwrite |
|
overwrite |
|
append |
|
add |
|
add |
|
overwrite |
|
overwrite |
|
overwrite |
|
append |
|
overwrite |
|
overwrite |
|
overwrite |
|
add |
|
overwrite |
|
overwrite |
|
overwrite |
|
overwrite |
|
overwrite |
|
overwrite |
|
overwrite |
|
overwrite |
Example 1: Policy statement configuration
{
"rtbrick-config:policy": {
"statement": [
{
"name": "EXPORT_POLICY1",
"ordinal": [
{
"ordinal": 10,
"description": "Add BGP community to direct routes",
"match-logic": "and",
"match": {
"rule": [
{
"rule": 1,
"type": "ipv6-prefix",
"value-type": "discrete",
"match-type": "or-longer",
"value": "2001:db8:0:60::/32"
},
{
"rule": 2,
"type": "source",
"value-type": "discrete",
"match-type": "exact",
"value": "direct"
}
]
},
"action": {
"rule": [
{
"rule": 1,
"type": "community",
"operation": "append",
"value": "100:1"
},
{
"rule": 2,
"operation": "return-permit"
}
]
}
},
{
"ordinal": 20,
"description": "Allow any other route",
"action": {
"rule": [
{
"rule": 1,
"operation": "return-permit"
}
]
}
}
]
}
]
}
}
Example 2: Policy statement configuration for RPKI Validation State Overwrite
{
"rtbrick-config:policy": {
"statement": [
{
"name": "S1",
"ordinal": [
{
"ordinal": 1,
"match-logic": "and",
"match": {
"rule": [
{
"rule": 1,
"type": "rpki-validation-state",
"value-type": "discrete",
"match-type": "exact",
"value": [
"invalid"
]
},
{
"rule": 2,
"type": "ipv4-prefix",
"value-type": "discrete",
"match-type": "exact",
"value": [
"192.168.0.11/32"
]
}
]
},
"action": {
"rule": [
{
"rule": 1,
"type": "rpki-validation-state",
"operation": "overwrite",
"value": [
"unknown"
]
},
{
"rule": 2,
"operation": "return-permit"
}
]
}
}
]
}
]
}
}
Configuring Policy Lists
Syntax:
| Attribute | Description |
|---|---|
|
Name of the policy list |
|
Type of the policy list. The following types of lists are supported: - as-path |
|
The number of the list entry. |
|
The value of the list entry, for example an IP prefix, or a community. |
Example: Policy list configuration
{
"rtbrick-config:policy": {
"list": [
{
"name": "PREFIX_LIST1",
"type": "ipv6-prefix",
"ordinal": [
{
"ordinal": 1,
"value": "2001:db8:0:10::/32"
},
{
"ordinal": 2,
"value": "2001:db8:0:25::/32"
},
{
"ordinal": 3,
"value": "2001:db8:0:30::/32"
}
]
}
]
}
}
Example: Optimising AS-path Matching
The "neighbor" match-type specifically targets the AS number of the neighboring peer in the RIB entry. For example, the following configuration matches RIB entries whose neighbor AS number is in the "as_neighbor_list", such as 100, 200, or 300.
set policy list as_neighbor_list as-path set policy list as_neighbor_list as-path ordinal 1 set policy list as_neighbor_list as-path ordinal 1 value 100 set policy list as_neighbor_list as-path ordinal 2 set policy list as_neighbor_list as-path ordinal 2 value 200 set policy list as_neighbor_list as-path ordinal 3 set policy list as_neighbor_list as-path ordinal 3 value 300 set policy statement IMPORT_POLICY set policy statement IMPORT_POLICY ordinal 1 set policy statement IMPORT_POLICY ordinal 1 match set policy statement IMPORT_POLICY ordinal 1 match rule 1 set policy statement IMPORT_POLICY ordinal 1 match rule 1 type as-path set policy statement IMPORT_POLICY ordinal 1 match rule 1 value-type list set policy statement IMPORT_POLICY ordinal 1 match rule 1 match-type neighbor set policy statement IMPORT_POLICY ordinal 1 match rule 1 value as_neighbor_list set policy statement IMPORT_POLICY ordinal 1 action set policy statement IMPORT_POLICY ordinal 1 action rule 1 set policy statement IMPORT_POLICY ordinal 1 action rule 1 operation return-deny
The "origin" match-type matches for origin as-path number. For example, the following configuration matches RIB entries whose origin AS number is in the "as_origin_list".
set policy list as_origin_list as-path set policy list as_origin_list as-path ordinal 1 set policy list as_origin_list as-path ordinal 1 value 125 set policy list as_origin_list as-path ordinal 2 set policy list as_origin_list as-path ordinal 2 value 225 set policy list as_origin_list as-path ordinal 3 set policy list as_origin_list as-path ordinal 3 value 325 set policy statement IMPORT_POLICY ordinal 2 set policy statement IMPORT_POLICY ordinal 2 match set policy statement IMPORT_POLICY ordinal 2 match rule 1 set policy statement IMPORT_POLICY ordinal 2 match rule 1 type as-path set policy statement IMPORT_POLICY ordinal 2 match rule 1 value-type list set policy statement IMPORT_POLICY ordinal 2 match rule 1 match-type origin set policy statement IMPORT_POLICY ordinal 2 match rule 1 value as_origin_list set policy statement IMPORT_POLICY ordinal 2 action set policy statement IMPORT_POLICY ordinal 2 action rule 1 set policy statement IMPORT_POLICY ordinal 2 action rule 1 operation return-deny
The "transit" match-type matches for AS numbers in rib-entry excluding neighbor and origin.
set policy list as_transit_list as-path set policy list as_transit_list as-path ordinal 1 set policy list as_transit_list as-path ordinal 1 value 150 set policy list as_transit_list as-path ordinal 2 set policy list as_transit_list as-path ordinal 2 value 250 set policy list as_transit_list as-path ordinal 3 set policy list as_transit_list as-path ordinal 3 value 350 set policy statement IMPORT_POLICY ordinal 3 set policy statement IMPORT_POLICY ordinal 3 match set policy statement IMPORT_POLICY ordinal 3 match rule 1 set policy statement IMPORT_POLICY ordinal 3 match rule 1 type as-path set policy statement IMPORT_POLICY ordinal 3 match rule 1 value-type list set policy statement IMPORT_POLICY ordinal 3 match rule 1 match-type transit set policy statement IMPORT_POLICY ordinal 3 match rule 1 value as_transit_list set policy statement IMPORT_POLICY ordinal 3 action set policy statement IMPORT_POLICY ordinal 3 action rule 1 set policy statement IMPORT_POLICY ordinal 3 action rule 1 operation return-deny
The sub-type "range" allows configuring a range of AS path values. The policy list supports sub-type "range" and ordinal value "value2", which are supported only for AS-path. When sub-type "range" is configured, the "value" (minimum value) and "value2" (maximum value) must be configured.
set policy list BOGON_ASNS as-path set policy list BOGON_ASNS as-path sub-type range set policy list BOGON_ASNS as-path ordinal 1 set policy list BOGON_ASNS as-path ordinal 1 value 0 set policy list BOGON_ASNS as-path ordinal 1 value2 0 set policy list BOGON_ASNS as-path ordinal 2 set policy list BOGON_ASNS as-path ordinal 2 value 23456 set policy list BOGON_ASNS as-path ordinal 2 value2 23456 set policy list BOGON_ASNS as-path ordinal 3 set policy list BOGON_ASNS as-path ordinal 3 value 64496 set policy list BOGON_ASNS as-path ordinal 3 value2 64511 set policy list BOGON_ASNS as-path ordinal 4 set policy list BOGON_ASNS as-path ordinal 4 value 65536 set policy list BOGON_ASNS as-path ordinal 4 value2 65551 set policy list BOGON_ASNS as-path ordinal 5 set policy list BOGON_ASNS as-path ordinal 5 value 4200000000 set policy list BOGON_ASNS as-path ordinal 5 value2 4294967294 set policy list BOGON_ASNS as-path ordinal 6 set policy list BOGON_ASNS as-path ordinal 6 value 65535 set policy list BOGON_ASNS as-path ordinal 6 value2 65535 set policy list BOGON_ASNS as-path ordinal 7 set policy list BOGON_ASNS as-path ordinal 7 value 4294967294 set policy list BOGON_ASNS as-path ordinal 7 value2 4294967294 set policy list BOGON_ASNS as-path ordinal 8 set policy list BOGON_ASNS as-path ordinal 8 value 65552 set policy list BOGON_ASNS as-path ordinal 8 value2 131071 set policy statement BOGON_ASN_FILTERING set policy statement BOGON_ASN_FILTERING ordinal 1 set policy statement BOGON_ASN_FILTERING ordinal 1 match set policy statement BOGON_ASN_FILTERING ordinal 1 match rule 1 set policy statement BOGON_ASN_FILTERING ordinal 1 match rule 1 type as-path set policy statement BOGON_ASN_FILTERING ordinal 1 match rule 1 value-type list set policy statement BOGON_ASN_FILTERING ordinal 1 match rule 1 match-type exists set policy statement BOGON_ASN_FILTERING ordinal 1 match rule 1 value BOGON_ASNS set policy statement BOGON_ASN_FILTERING ordinal 1 action set policy statement BOGON_ASN_FILTERING ordinal 1 action rule 1 set policy statement BOGON_ASN_FILTERING ordinal 1 action rule 1 operation return-deny
Also, network operators may need to match AS-path length to detect bogus announcements. For example, drop all AS-paths with lengths greater than 100. To support this, a new value type, "length" has been added, which supports the match type "greater-or-exact."
set policy statement CHECK_LENGTH set policy statement CHECK_LENGTH ordinal 1 set policy statement CHECK_LENGTH ordinal 1 match set policy statement CHECK_LENGTH ordinal 1 match rule 1 set policy statement CHECK_LENGTH ordinal 1 match rule 1 type as-path set policy statement CHECK_LENGTH ordinal 1 match rule 1 value-type length set policy statement CHECK_LENGTH ordinal 1 match rule 1 match-type greater-or-exact set policy statement CHECK_LENGTH ordinal 1 match rule 1 value 10 set policy statement CHECK_LENGTH ordinal 1 action set policy statement CHECK_LENGTH ordinal 1 action rule 1 set policy statement CHECK_LENGTH ordinal 1 action rule 1 operation return-permit
Configuring Policy Conditions
Policy conditions refer to certain states of the system represented in BDS tables. You need to specify the table, the daemon (BD) that needs to resolve the condition, and if applicable, the attributes used to define the condition.
There are two types of conditions:
-
Match on certain attributes in BDS table objects.
-
Match on the number of objects in a BDS table.
Configuring Table Match
Syntax:
| Attribute | Description |
|---|---|
|
Name of the policy condition |
|
Name of the BDS table |
|
Name of the BD which resolves the condition. Currently supported BDs are: ifmd, ribd, mribd, pppoed, subscriberd, ipoed, l2tpd, pimd, igmp.iod, isis.iod, ospf.appd ospf.iod |
|
Optionally, match on the number of objects in a table |
|
Type of match for an object count. Supported match types are: |
Configuring Attribute Match
You can configure attributes to define a condition. The attributes refer to objects in the table configured in the section above. Please note:
-
You can match on multiple attributes.
-
In order to identify matching objects, you need to specify all attributes which are primary keys in the table.
-
Attribute configuration is not required for conditions matching on the number of table objects using the
countoption.
Syntax:
| Attribute | Description |
|---|---|
|
Name of the policy condition |
|
Name of the attribute in the BDS table |
|
Value of the attribute to match |
|
Type of the match. Supported match types are: |
Example: Policy condition configuration
{
"rtbrick-config:policy": {
"condition": [
{
"condition_name": "precheck",
"table": {
"name": "global.instance",
"bd": "bgp.iod.1"
},
"attribute": [
{
"name": "instance_name",
"match": "equal",
"value": "default"
}
]
}
]
}
}
Attaching Policies
Once a policy has been created, they need to be applied to an application like a routing protocol to take effect.
BGP Attachment Points
-
Instance import/export
-
BGP peer group import/export
-
BGP redistribution
For attaching policies to the BGP protocol, please refer to the RBFS BGP User Guide.
IS-IS Attachment Points
-
IS-IS redistribution
For attaching policies to the IS-IS protocol, please refer to the IS-IS User Guide.
OSPFv2 Attachment Points
-
OSPFv2 redistribution
For attaching policies to the OSPFv2/v3 protocol, please refer to the OSPFv2 User Guide.
Policy Chaining Configuration
The following configuration demonstrates how policy chaining is applied for the PEERING_V4 BGP peer group. For IPv4 unicast address family, incoming routes will be evaluated and imported only if they meet the criteria defined in the associated import policies. These policies provide layered route filtering, ensuring that only valid and desired routes are accepted by the peer.
The configuration applies a series of import policies for the IPv4 unicast address family. These policies are chained in sequence, each performing specific tasks such as:
-
Filtering bogon IPs (FILTER_BOGONS_V4).
-
Preventing the import of the peer’s own IP ranges (FILTER_OWN_V4).
-
Scrubbing unwanted community tags (SCRUB_COMMUNITIES).
The following example shows the policy chaining configuration for the peer-group “PEERING_V4.”
set instance default protocol bgp peer-group PEERING_V4 set instance default protocol bgp peer-group PEERING_V4 remote-as 65536 set instance default protocol bgp peer-group PEERING_V4 address-family ipv4 labeled-unicast set instance default protocol bgp peer-group PEERING_V4 address-family ipv4 unicast set instance default protocol bgp peer-group PEERING_V4 address-family ipv4 unicast policy import FILTER_BOGONS_V4 set instance default protocol bgp peer-group PEERING_V4 address-family ipv4 unicast policy import FILTER_OWN_V4 set instance default protocol bgp peer-group PEERING_V4 address-family ipv4 unicast policy import SCRUB_COMMUNITIES
supervisor@rtbrick>SPINE01: cfg> show config instance default protocol bgp peer-group PEERING_V4
{
"rtbrick-config:peer-group": [
{
"pg-name": "PEERING_V4",
"remote-as": 65536,
"address-family": [
{
"afi": "ipv4",
"safi": "labeled-unicast"
},
{
"afi": "ipv4",
"safi": "unicast",
"policy": {
"import": [
"FILTER_BOGONS_V4",
"FILTER_OWN_V4",
"SCRUB_COMMUNITIES" ]
}
},
{
"afi": "ipv6",
"safi": "labeled-unicast"
},
{
"afi": "ipv6",
"safi": "unicast"
}
]
}
]
}
Policy Statement Configurations for Policy Chaining
The following configurations provide a detailed representation of the policy statements utilized in the aforementioned policy chaining example.
The example below shows the policy definitions for the FILTER_BOGONS_V4 policy statement.
set policy statement FILTER_BOGONS_V4 set policy statement FILTER_BOGONS_V4 ordinal 1 set policy statement FILTER_BOGONS_V4 ordinal 1 description FILTER_BOGONS set policy statement FILTER_BOGONS_V4 ordinal 1 match-logic or set policy statement FILTER_BOGONS_V4 ordinal 1 match set policy statement FILTER_BOGONS_V4 ordinal 1 match rule 1 set policy statement FILTER_BOGONS_V4 ordinal 1 match rule 1 type ipv4-prefix set policy statement FILTER_BOGONS_V4 ordinal 1 match rule 1 value-type list set policy statement FILTER_BOGONS_V4 ordinal 1 match rule 1 match-type or-longer set policy statement FILTER_BOGONS_V4 ordinal 1 match rule 1 value FILTER_BOGONS set policy statement FILTER_BOGONS_V4 ordinal 1 match rule 2 set policy statement FILTER_BOGONS_V4 ordinal 1 match rule 2 type ipv4-prefix set policy statement FILTER_BOGONS_V4 ordinal 1 match rule 2 value-type discrete set policy statement FILTER_BOGONS_V4 ordinal 1 match rule 2 match-type regex set policy statement FILTER_BOGONS_V4 ordinal 1 match rule 2 value 0.0.0.0/(2[5-9]|3[0-1]) set policy statement FILTER_BOGONS_V4 ordinal 1 action set policy statement FILTER_BOGONS_V4 ordinal 1 action rule 1 set policy statement FILTER_BOGONS_V4 ordinal 1 action rule 1 operation return-deny set policy statement FILTER_BOGONS_V4 ordinal 2 set policy statement FILTER_BOGONS_V4 ordinal 2 description FILTER_IXP set policy statement FILTER_BOGONS_V4 ordinal 2 match set policy statement FILTER_BOGONS_V4 ordinal 2 match rule 1 set policy statement FILTER_BOGONS_V4 ordinal 2 match rule 1 type ipv4-prefix set policy statement FILTER_BOGONS_V4 ordinal 2 match rule 1 value-type list set policy statement FILTER_BOGONS_V4 ordinal 2 match rule 1 match-type or-longer set policy statement FILTER_BOGONS_V4 ordinal 2 match rule 1 value IXP_PEERING_LANS_V4 set policy statement FILTER_BOGONS_V4 ordinal 2 action set policy statement FILTER_BOGONS_V4 ordinal 2 action rule 1 set policy statement FILTER_BOGONS_V4 ordinal 2 action rule 1 operation return-deny
The example below shows the configurations of the ‘FILTER_BOGONS’ policy list used in the ‘FILTER_BOGONS_V4’ policy statement.
supervisor@S1-STD-2-2004>bm04-tst.fsn.rtbrick.net: op> show config set policy list FILTER_BOGONS set policy list FILTER_BOGONS ipv4-prefix set policy list FILTER_BOGONS ipv4-prefix ordinal 1 set policy list FILTER_BOGONS ipv4-prefix ordinal 1 value 0.0.0.0/8 set policy list FILTER_BOGONS ipv4-prefix ordinal 2 set policy list FILTER_BOGONS ipv4-prefix ordinal 2 value 10.0.0.0/8 set policy list FILTER_BOGONS ipv4-prefix ordinal 3 set policy list FILTER_BOGONS ipv4-prefix ordinal 3 value 100.64.0.0/10 set policy list FILTER_BOGONS ipv4-prefix ordinal 4 set policy list FILTER_BOGONS ipv4-prefix ordinal 4 value 127.0.0.0/8
The example below shows the configurations of the ‘IXP_PEERING_LANS_V4’ policy list used in the ‘FILTER_BOGONS_V4’ policy statement.
set policy list IXP_PEERING_LANS_V4 ipv4-prefix set policy list IXP_PEERING_LANS_V4 ipv4-prefix ordinal 1 set policy list IXP_PEERING_LANS_V4 ipv4-prefix ordinal 1 value 80.81.192.0/21 set policy list IXP_PEERING_LANS_V4 ipv4-prefix ordinal 2 set policy list IXP_PEERING_LANS_V4 ipv4-prefix ordinal 2 value 80.249.208.0/21 set policy list IXP_PEERING_LANS_V4 ipv4-prefix ordinal 3 set policy list IXP_PEERING_LANS_V4 ipv4-prefix ordinal 3 value 91.213.211.0/24 set policy list IXP_PEERING_LANS_V4 ipv4-prefix ordinal 4 set policy list IXP_PEERING_LANS_V4 ipv4-prefix ordinal 4 value 185.0.20.0/23
The example below shows the policy definitions for the FILTER_OWN_V4 policy statement.
set policy statement FILTER_OWN_V4 set policy statement FILTER_OWN_V4 ordinal 1 set policy statement FILTER_OWN_V4 ordinal 1 match set policy statement FILTER_OWN_V4 ordinal 1 match rule 1 set policy statement FILTER_OWN_V4 ordinal 1 match rule 1 type ipv4-prefix set policy statement FILTER_OWN_V4 ordinal 1 match rule 1 value-type list set policy statement FILTER_OWN_V4 ordinal 1 match rule 1 match-type or-longer set policy statement FILTER_OWN_V4 ordinal 1 match rule 1 value MYPREFIXES_V4 set policy statement FILTER_OWN_V4 ordinal 1 action set policy statement FILTER_OWN_V4 ordinal 1 action rule 1 set policy statement FILTER_OWN_V4 ordinal 1 action rule 1 operation return-deny
The example below shows the configurations of the ‘MYPREFIXES_V4’ policy list used in the ‘FILTER_OWN_V4’ policy statement.
set policy list MYPREFIXES_V4 ipv4-prefix set policy list MYPREFIXES_V4 ipv4-prefix ordinal 1 set policy list MYPREFIXES_V4 ipv4-prefix ordinal 1 value 192.0.2.0/24 set policy list MYPREFIXES_V4 ipv4-prefix ordinal 2 set policy list MYPREFIXES_V4 ipv4-prefix ordinal 2 value 198.51.100.0/24 set policy list MYPREFIXES_V4 ipv4-prefix ordinal 3 set policy list MYPREFIXES_V4 ipv4-prefix ordinal 3 value 203.0.113.0/24
The example below shows the policy definitions for the SCRUB_COMMUNITIES policy statement.
set policy statement SCRUB_COMMUNITIES set policy statement SCRUB_COMMUNITIES ordinal 1 set policy statement SCRUB_COMMUNITIES ordinal 1 match set policy statement SCRUB_COMMUNITIES ordinal 1 match rule 1 set policy statement SCRUB_COMMUNITIES ordinal 1 match rule 1 type community set policy statement SCRUB_COMMUNITIES ordinal 1 match rule 1 value-type discrete set policy statement SCRUB_COMMUNITIES ordinal 1 match rule 1 match-type regex set policy statement SCRUB_COMMUNITIES ordinal 1 match rule 1 value 64496:* set policy statement SCRUB_COMMUNITIES ordinal 1 action set policy statement SCRUB_COMMUNITIES ordinal 1 action rule 1 set policy statement SCRUB_COMMUNITIES ordinal 1 action rule 1 type community set policy statement SCRUB_COMMUNITIES ordinal 1 action rule 1 operation delete-attribute-match set policy statement SCRUB_COMMUNITIES ordinal 1 action rule 2 operation return-permit
Sample Configurations
Example 1: BGP export policy referencing a policy list
supervisor@leaf1: cfg> show config policy
{
"rtbrick-config:policy": {
"list": [
{
"name": "PREFIX_LIST2",
"type": "ipv6-prefix",
"ordinal": [
{
"ordinal": 1,
"value": "2001:db8:0:60::/32"
},
{
"ordinal": 2,
"value": "2001:db8:0:80::/64"
},
{
"ordinal": 3,
"value": "2001:db8:0:110::/64 "
}
]
}
],
"statement": [
{
"name": "EXPORT_POLICY2",
"ordinal": [
{
"ordinal": 10,
"description": "Add community to direct routes",
"match": {
"rule": [
{
"rule": 1,
"type": "source",
"value-type": "discrete",
"match-type": "exact",
"value": "direct"
}
]
},
"action": {
"rule": [
{
"rule": 1,
"type": "community",
"operation": "append",
"value": "100:1"
},
{
"rule": 2,
"operation": "return-permit"
}
]
}
},
{
"ordinal": 20,
"description": "Allow list of routes",
"match": {
"rule": [
{
"rule": 1,
"type": "ipv6-prefix",
"value-type": "list",
"match-type": "or-longer",
"value": "PREFIX_LIST2"
}
]
},
"action": {
"rule": [
{
"rule": 1,
"operation": "return-permit"
}
]
}
},
{
"ordinal": 30,
"description": "Deny any other route",
"action": {
"rule": [
{
"rule": 1,
"operation": "return-deny"
}
]
}
}
]
}
]
}
}
supervisor@leaf1: cfg> show config instance default protocol bgp peer-group spine address-family ipv6 unicast
{
"rtbrick-config:address-family": [
{
"afi": "ipv6",
"safi": "unicast",
"policy": {
"export": "EXPORT_POLICY2"
}
}
]
}
Example 2: IGMP filter policy
supervisor@leaf1: cfg> show config policy
{
"rtbrick-config:policy": {
"statement": [
{
"name": "IGMP_FILTER",
"ordinal": [
{
"ordinal": 1,
"description": "IGMP group filter",
"match-logic": "or",
"match": {
"rule": [
{
"rule": 1,
"type": "ipv4-mcast-group",
"value-type": "discrete",
"match-type": "or-longer",
"value": "198.51.100.0/24"
},
{
"rule": 2,
"type": "ipv4-mcast-group",
"value-type": "discrete",
"match-type": "or-longer",
"value": "198.51.100.0/24"
}
]
},
"action": {
"rule": [
{
"rule": 1,
"operation": "return-permit"
}
]
}
}
]
}
]
}
}
supervisor@leaf1: cfg> show config multicast-options igmp
{
"rtbrick-config:igmp": {
"interface-profile": [
{
"profile-name": "PROFILE1",
"filter-policy": "IGMP_FILTER"
}
]
}
}
Example 4: Community Deletion Configuration
supervisor@rtbrick: cfg> show config policy
{
"rtbrick-config:policy": {
"statement": [
{
"name": "test_policy",
"ordinal": [
{
"ordinal": 1,
"match-logic": "or",
"match": {
"rule": [
{
"rule": 1,
"type": "community",
"value-type": "discrete",
"match-type": "exists",
"value": [
"1:1"
]
},
{
"rule": 2,
"type": "extended-community",
"value-type": "discrete",
"match-type": "exists",
"value": [
"target:3.3.3.3:3000",
"target:5.5.5.5:5000"
]
},
{
"rule": 3,
"type": "large-community",
"value-type": "discrete",
"match-type": "exists",
"value": [
"3333:33333:33",
"4444:44444:44"
]
},
{
"rule": 4,
"type": "community",
"value-type": "discrete",
"match-type": "regex",
"value": [
"555:*"
]
}
]
},
"action": {
"rule": [
{
"rule": 1,
"type": "community",
"operation": "delete-attribute-match"
},
{
"rule": 2,
"type": "extended-community",
"operation": "delete-attribute-match"
},
{
"rule": 3,
"type": "large-community",
"operation": "delete-attribute-match"
},
{
"rule": 4,
"operation": "return-permit"
}
]
}
}
]
}
]
}
}
Matching ARP-ND Source in Policy
The example below configures a policy statement named ARP_ND_SOURCE_MATCH. It defines a rule (ordinal 1) that matches traffic of type arp-nd and appends the community 111:111 to it, with a final rule (ordinal 99) set to permit all other traffic.
set policy statement ARP_ND_SOURCE_MATCH set policy statement ARP_ND_SOURCE_MATCH ordinal 1 set policy statement ARP_ND_SOURCE_MATCH ordinal 1 description ARP_ND_POLICY_SOURCE_COM_ADD set policy statement ARP_ND_SOURCE_MATCH ordinal 1 match set policy statement ARP_ND_SOURCE_MATCH ordinal 1 match rule 1 set policy statement ARP_ND_SOURCE_MATCH ordinal 1 match rule 1 type source set policy statement ARP_ND_SOURCE_MATCH ordinal 1 match rule 1 value-type discrete set policy statement ARP_ND_SOURCE_MATCH ordinal 1 match rule 1 match-type exact set policy statement ARP_ND_SOURCE_MATCH ordinal 1 match rule 1 value arp-nd set policy statement ARP_ND_SOURCE_MATCH ordinal 1 action set policy statement ARP_ND_SOURCE_MATCH ordinal 1 action rule 1 set policy statement ARP_ND_SOURCE_MATCH ordinal 1 action rule 1 type community set policy statement ARP_ND_SOURCE_MATCH ordinal 1 action rule 1 operation append set policy statement ARP_ND_SOURCE_MATCH ordinal 1 action rule 1 value 111:111 set policy statement ARP_ND_SOURCE_MATCH ordinal 99 set policy statement ARP_ND_SOURCE_MATCH ordinal 99 action set policy statement ARP_ND_SOURCE_MATCH ordinal 99 action rule 99 set policy statement ARP_ND_SOURCE_MATCH ordinal 99 action rule 99 operation return-permit
{
"rtbrick-config:statement": [
{
"name": "ARP_ND_SOURCE_MATCH",
"ordinal": [
{
"ordinal": 1,
"description": "ARP_ND_POLICY_SOURCE_COM_ADD",
"match": {
"rule": [
{
"rule": 1,
"type": "source",
"value-type": "discrete",
"match-type": "exact",
"value": [
"arp-nd"
]
}
]
},
"action": {
"rule": [
{
"rule": 1,
"type": "community",
"operation": "append",
"value": [
"111:111"
]
}
]
}
},
{
"ordinal": 99,
"action": {
"rule": [
{
"rule": 99,
"operation": "return-permit"
}
]
}
}
]
}
]
}