RBFS Overview
RBFS At-a-Glance
RtBrick Full Stack (RBFS) is a carrier-grade network operating system developed specifically for disaggregated telco networks. It supports deployments ranging from small local carriers to Tier 1 to Tier 4 operators, meeting stringent scalability, reliability, and performance requirements. By disaggregating software from hardware, RBFS helps operators modernize their infrastructure without being locked into proprietary systems. It is deployed on bare-metal switches and transforms them into fully functional and programmable routing platforms. These platforms are capable of implementing a broad set of use cases across broadband access, edge, metro, CGNAT, and peering network segments.
RBFS can be operated in a variety of roles within the network. These include its use as a Broadband Network Gateway (BNG) for subscriber termination, as a peering router in the operator’s core, or as a system supporting integrated Carrier-Grade NAT (CGNAT) functionality. This role flexibility makes it suitable for both centralized and distributed deployments in modern telecom architectures.
Modular and Resilient Architecture
RBFS has been built around a modular, microservice-oriented architecture. Each protocol or service runs independently as an isolated process, providing high fault isolation and resilience. This architecture simplifies lifecycle operations such as updates, restarts, and diagnostics. For example, individual components can be restarted without requiring a system-wide reboot or service interruption.
A key element of this design is the distributed datastore known as the Brick Datastore (BDS). This datastore ensures that configuration and operational state are consistently available to all modules. Deterministic behavior is achieved through this shared state, enabling reliable operation and support for advanced functions such as transactional configuration, rollback, and state persistence across restarts.
Automation and Management Interfaces
RBFS integrates with industry-standard management interfaces and protocols, including CLI, NETCONF, RESTCONF/YANG, gNMI, RESTful APIs, and telemetry streaming. All configuration and operational data are modeled using YANG or OpenAPI, enabling full automation and lifecycle management through external systems. This allows seamless integration into orchestration platforms, provisioning systems, or in-house tooling, supporting both push and pull models.
Support is provided for both synchronous and asynchronous workflows, allowing operators to manage thousands of devices consistently at scale. Built-in support for Prometheus streaming further enhances observability and troubleshooting capabilities. RBFS provides fine-grained access controls and audit mechanisms to support secure operations in multi-team environments.
Comprehensive Feature Set
RBFS supports a wide range of access and aggregation technologies. These include traditional technologies such as PPPoE and L2TPv2 (LAC), as well as IPoE over DHCPv4 and DHCPv6 for modern broadband deployments. The platform offers complete BNG functionality, including DHCP proxy and relay modes, dynamic subscriber session handling, and seamless IP address management.
Advanced features such as hierarchical quality of service (HQoS), multicast replication for IPTV, full CGNAT with high bandwidth scalability, and support for Lawful Interception are included in the base system. The system is also equipped to support dual-stack IPv4 and IPv6 services, ensuring readiness for evolving network requirements.
RBFS also includes mechanisms for stateful redundancy, both Active/Active and Active/Standby, and fast failover, enabling uninterrupted service delivery in large-scale environments. Combined with flexible traffic steering and policy enforcement, RBFS provides a robust foundation for broadband and edge services.
Hardware Flexibility and Ecosystem
RBFS has been validated on a wide range of white-box platforms powered by merchant silicon, including devices from UfiSpace and Edgecore. The operating system runs on OCP-compliant switches, making it compatible with various hardware vendors.
This disaggregation of hardware and software enables operators to optimize both capital and operational expenditures. Devices can be selected based on specific performance, port density, and energy efficiency needs, while the RBFS software stack provides a consistent set of features and interfaces across the network. This approach aligns with the industry’s shift toward cloud-native, software-defined infrastructure.
RBFS delivers the flexibility, scalability, and feature richness required to support the transformation of traditional telecom networks into fully disaggregated, automated, and programmable infrastructures.
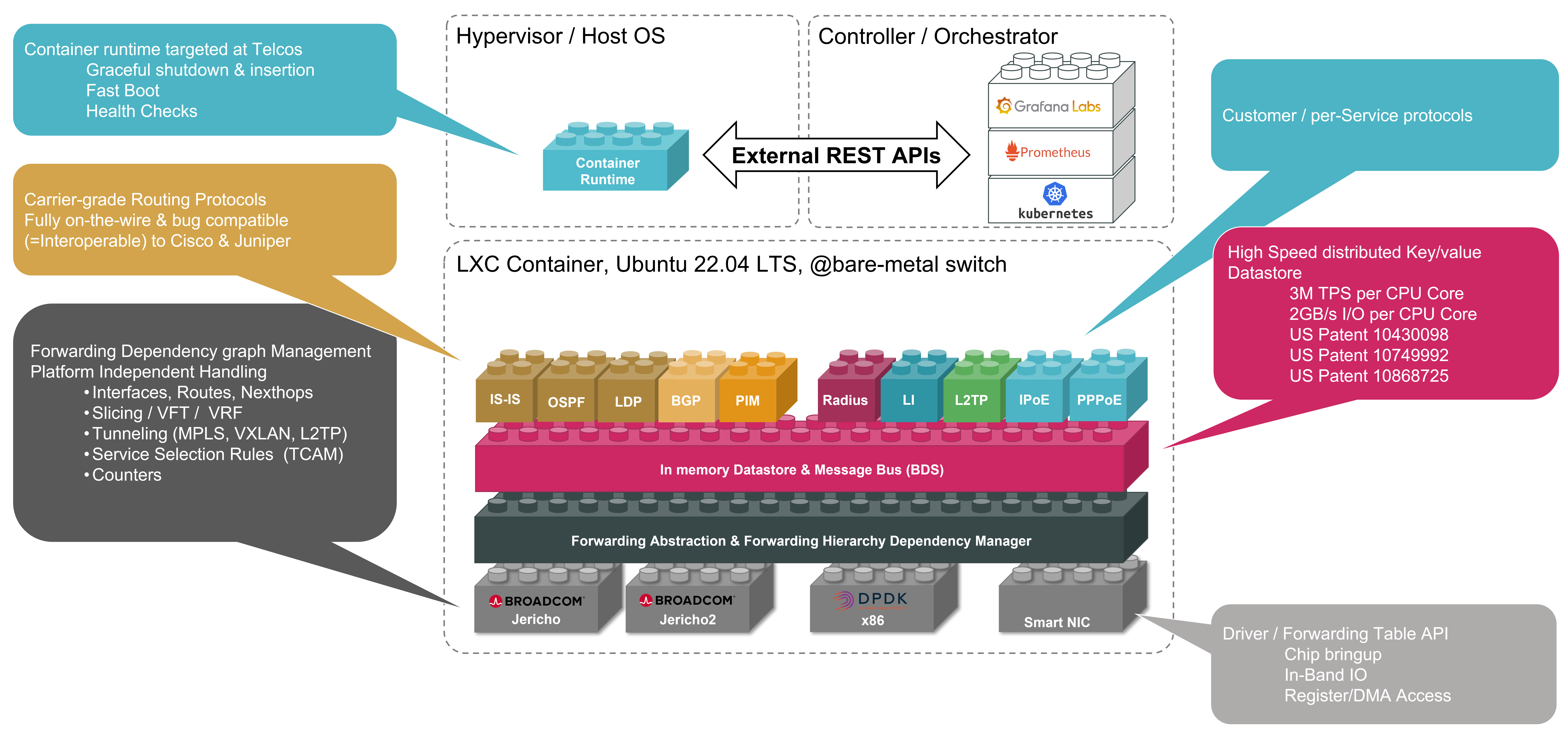
Why RBFS
RBFS has been designed to address the operational, economic, and architectural challenges of modern service provider networks. Its open and disaggregated design enables the rapid introduction of new features and services, while fostering a collaborative and competitive ecosystem of hardware, silicon, and software vendors.
By disaggregating software from hardware, RBFS gives operators the freedom to choose white-box switches based on technical or commercial criteria, avoiding vendor lock-in and reducing hardware dependency. This disaggregated approach significantly lowers both capital and operational expenditures. It supports cloud-native deployment models, making it particularly suitable for environments that require elasticity, programmability, and seamless integration into DevOps pipelines.
RBFS is built on a cloud-native microservices architecture, offering major advantages over traditional monolithic systems. Each application is isolated into its own process, which allows for independent scaling and fault isolation. This architecture provides greater agility and simplifies the deployment of software updates and new features without affecting overall system stability.
Operational efficiency is further enhanced by native support for automation and observability. This accelerates innovation and reduces operational overhead.
With its ability to meet the technical requirements for diverse networks, RBFS represents a future-proof platform that combines performance, openness, and automation in a single solution.
Architecture and the Key Functional Components
RBFS has been designed based on a microservices architecture to cater a rapidly growing broadband traffic. An RBFS container contains multiple microservices, known as daemons. These microservices are the building blocks of the RBFS ecosystem and they can communicate with each other through a centralized in-memory datastore called Brick Data Store (BDS).
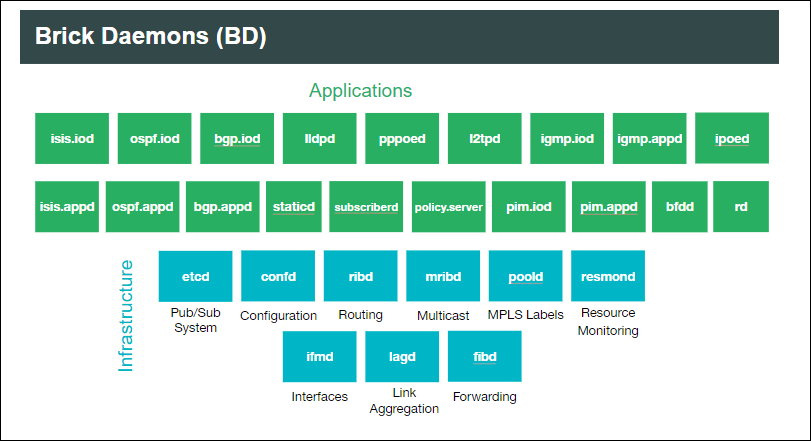
Brick Data Store
RBFS has a schema-driven and in-memory database called BDS (Brick Data Store). As an in-memory data store, BDS relies mainly on the main memory for the storage of data which is contrary to the databases that store data on disks. BDS has architecturally been designed to enable very minimal response time by removing the time to access data stored in disks. BDS acts as a control plane and provides all required data and instructions to the daemons for their functioning.
Brick Microservices
RBFS’s microservices architecture enables it to perform various complementary functions and deliver services.
For example, the subscriber microservice (subscriberd) manages the current subscriber state and is responsible for authentication, authorization, and accounting. The ribd microservice is responsible for route selection, next-hop resolution, tunnel selection and recursion.
There are microservices such as CtrlD (Controller) and ApiGwD (API Gateway) which are part of the RBFS ecosystem. These daemons sit in the middle (on the Host System) and manage all the communication between the client and backend services running in the container. The API Gateway (ApiGwD) microservice provides a single point access to expose services running inside of the RBFS container.
RBFS microservice and other dependencies are packaged as a Debian LXC container. The RBFS container is hosted on the RtBrick Host , an open-source operating system, which can be run on white box switches.
RBFS can perform various roles such as Spine, Leaf, and Multiservice Edge which serve different use-cases. The software images of these various roles contain daemons that are required to serve these roles for their different functions. The RBFS Multiservice Edge software image contains all the RBFS daemons packaged in a container, other roles such as Spine and Leaf include only the daemons which are required to carry out their respective functions. For example, the Spine image includes (in addition to other daemons) the interior gateway protocol daemons such as isis.appd, isis.iod, ospf.appd, and ospf.iod which are not required in the Leaf image.
The daemons such as alertmanager, confd, etcd, fibd, hostconfd, ifmd and so on are present in the images of both the Spine and Leaf roles as these daemons are required in both of these roles.
Containerization of Daemons
RBFS daemons and other dependencies are packaged as a Debian LXC container. This containerization is a logical layer that helps to make the applications secure, flexible, and portable by providing isolation. This RBFS container is hosted on the RtBrick Host, Debian-based operating system, which can be run on white box switches.
RBFS can perform various roles such as Spine, Leaf, and Multiservice Edge which have different functions to serve. The software images of these various roles contain daemons that are required to serve these roles for their different functions. Though, the RBFS Multiservice Edge software image contains all the RBFS daemons packaged in a container, other roles such as Spine and Leaf include only the daemons which are required to carry out their respective functions.
Launching Microservices Dynamically
When the RBFS container starts up, it installs different sets of microservices depending on the image role and platform. This is done to minimize resource consumption. In RBFS, the microservices are divided into two categories: base microservices and on-demand microservices. RBFS containers will have all microservices installed according to the platform and image role, but not all will be enabled on bootup. Only the base microservices will be enabled and started on bootup. On-demand microservices will only be started when their respective configurations are configured and will stop once all dependent configurations are deleted.
For instance, when the user configures BGP with the CLI command set instance
<instance> protocol bgp, the rtbrick-bgp.appd.1 and rtbrick-bgp.iod.1 services will start. And, once the BGP configuration is deleted, "rtbrick-bgp.appd.1" and "rtbrick-bgp.iod.1" will be stopped after 5 minutes (graceful shutdown time).
By default, the following base microservices will be running in the container.
-
rtbrick-confd
-
rtbrick-etcd
-
rtbrick-fibd
-
rtbrick-hostconfd
-
rtbrick-ifmd
-
rtbrick-lldpd
-
rtbrick-mribd
-
rtbrick-opsd
-
rtbrick-poold
-
rtbrick-resmond
-
rtbrick-resmond-agent
-
rtbrick-restconfd
-
rtbrick-ribd
-
rtbrick-staticd
When you make other RBFS configurations, the required on-demand microservices will be automatically enabled.
Supported Topologies
RBFS can be deployed in a spine-leaf architecture and can also be deployed standalone in a single switch which consolidates all the features in one switch.
A Multiservice Edge architecture offers all the functionalities of a spine-leaf BNG architecture on a single bare-metal switch.
A spine-leaf architecture is a two-tier network topology that consists of two switching layers — a spine and a leaf. In this topology, two layers of switches interconnect. The leaf layer consists of access switches that aggregate traffic and connect directly to the spine which is the core network.
The RBFS spine-leaf topology provides better scalability. This topology enables horizontal scaling by adding additional switches to add more capacity to handle increased traffic. This topology is also useful for higher bandwidth.
Interfaces to Operate and Manage RBFS
RBFS provides a CLI and a rich set of commands that you can use to operate, configure, monitor, and manage the system and its various components. Using the RBFS CLI, you can configure static IPv4, IPv6, MPLS, and multicast routes.
In addition to the CLI, RBFS also offers industry-standard tools and utilities such as RESTCONF/YANG.
RBFS supports REST-based industry-standard tools such as RESTCONF/YANG and Operational State API to enable communication with the software and underlying devices. RESTCONF is a programmatic interface that enables you to programmatically access RBFS devices and manage configurations.
The Operational State API microservice (opsd) provides the operation state of the system. It forms a stable contract between RBFS and network management systems and inspects the operational state of the device to diagnose and troubleshoot problems.
RBFS APIs allow to access and consume RBFS data simply and securely.
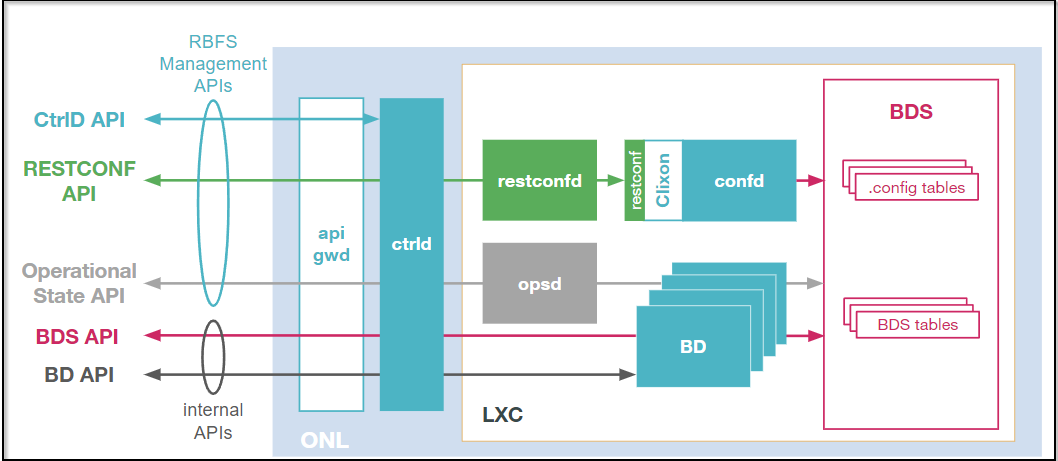
Features and Components
Routing
RBFS, at its core, is a routing software that supports both IP routing and MPLS routing. In dynamic IP routing, RBFS supports all major routing protocols that include OSPFv2 and IS-IS (interior gateway protocols) and BGP (exterior gateway protocol).
RBFS also supports Protocol Independent Multicast (PIM), a multicast routing protocol that runs over existing unicast infrastructure. PIM-SSM uses a subset of PIM sparse mode and IGMP to permit a client to receive multicast traffic directly from the source.
BGP
BGP is a standard exterior gateway protocol (EGP) supported by RtBrick. BGP is considered a “Path Vector” routing protocol and maintains a separate routing table based on the shortest Autonomous System (AS) path and various other route attributes.
IS-IS
IS-IS, or Intermediate System to Intermediate System, is an open standard routing protocol. ISO published the standard as a way to route datagrams as part of their OSI stack. IETF later republished the standard, and added IP route support.
OSPFv2/v3
OSPF (Open Shortest Path First) is an Interior Gateway Protocol that distributes routing information within a single Autonomous System (AS) in an IP network. OSPF is a link-state routing protocol that uses link-state information to form a routing table and exchange the routing information with the neighbors.
RtBrick FullStack (RBFS) supports OSPF version 2 (OSPFv2) and OSPF version 3 (OSPFv3), including authentication, LDP-IGP sync, and redistribution policy. RBFS does not support OSPFv3 Virtual Link.
LDP
Label distribution protocol (LDP) is the most commonly used protocol in the MPLS network. It generates and distributes labels and thus helps in MPLS packet switching and forwarding. By using LDP, label-switching routers in an MPLS network can exchange label mapping information to create label-switched paths (LSPs) for switching data packets. RtBrick FullStack (RBFS) supports Dual-stack, which means LDP can exchange FEC-label bindings over either IPv4 or IPv6 networks.
Segment Routing
RBFS supports segment routing using the IS-IS and OSPF protocols. In segment routing, the source router decides the path (throughout the network) to the destination and encodes the path details in the packet header as an ordered list of instructions. The routers on the path do not take any forwarding decisions but just execute the forwarding instructions.
Layer 2 Services
L2X
Layer 2 Cross-Connect (L2X) is a data plane feature that connects two physical ports (IFPs) using Layer 2 switching. L2X can switch the traffic between two IFPs to provide the trunk service for an Ethernet switch.
EVPN-VPWS
Ethernet Virtual Private Network (EVPN) is a Layer 2 internetworking technology similar to BGP/MPLS IP VPN. EVPN uses extended BGP reachability information and advertisements between different Layer 2 networks at various sites in the control plane.
The EVPN Virtual Private Wire Service (VPWS) is a point-to-point (P2P) service that is built on the EVPN service architecture. EVPN-VPWS uses MPLS tunnels to traverse the backbone network. It offers a Layer 2 packet forwarding mode that connects access circuits (ACs) as per the specifications of RFC 8214.
BGP-signaled L2VPN
The BGP-signaled L2VPN uses BGP for signaling and auto-discovery to establish multipoint Layer 2 VPN over the MPLS backbone network. The remote cross-connect is a point-to-point (P2P) service that connects two locations using the MPLS core network and MP-BGP. The remote cross-connect uses MPLS tunnels to traverse the backbone network. It offers a Layer 2 packet forwarding mode that connects access circuits (ACs). The RBFS implementation of BGP-signaled L2VPN is in accordance with RFC-6624 which supports L2VPN using BGP for auto-discovery and Signaling.
Multicast
IGMP
Internet Group Management (IGMP) protocol allows a host to advertise its multicast group membership to neighboring switches and routers. IGMP is a standard protocol used by the TCP/IP protocol suite to achieve dynamic multicasting.
PIM
PIM SSM builds shortest-path trees (SPTs) rooted at the source immediately because in SSM, the router closest to the interested receiver host is informed of the unicast IP address of the source for the multicast traffic. That is, PIM SSM bypasses the RP connection stage through shared distribution trees, as in PIM sparse mode, and goes directly to the source-based distribution tree.
Multicast VPN
The Multicast VPN (MVPN) feature provides the ability to support multicast over a Layer 3 VPN. Multicast allows the efficient distribution of information between a single multicast source and multiple receivers. IP multicast is used to stream video, voice, and data to an MPLS VPN network core. The RBFS MVPN implementation is based on RFC 6513 “Multicast in MPLS/BGP IP VPNs” and RFC 6514 “BGP Encodings and Procedures for Multicast in MPLS/BGP IP VPNs”.
Routing Policy
RBFS routing policies allow to control and modify the behavior of routing protocols such as IS-IS, OSPF, and BGP. RBFS has a generic routing policy framework that serves multiple purposes and applications. In RBFS, the routing policy implementation is performed by four major components: Policy Repository, Command Processing Module, Policy Server, and Policy Client.
Access and Subscriber Management
RtBrick’s modular and scalable subscriber management offers the next-generation access infrastructure (ng-access) that supports protocols such as PPPoE, IPoE, L2TPv2, DHCPv4 and DHCPv6 and RADIUS. It provides subscriber authentication, access, service creation, activation, and deactivation. It collects accounting statistics for the subscriber sessions. RBFS enables you to address the challenges such as interoperability with numerous client devices from various vendors which requires a well-implemented and industry-proven access protocol stack, including support for all relevant RFCs. RBFS subscriber management infrastructure provides the next generation of internet access protocols designed for carrier-grade services.
Support for PPPoE, IPoE, and L2TPv2
RBFS supports subscriber session management protocols such as Point-to-Point Protocol over Ethernet (PPPoE), Layer Two Tunneling Protocol (L2TPv2), and IP over Ethernet (IPoE) to deliver network access services to broadband subscribers.
PPPoE establishes a PPP connection over the ethernet. In RBFS, the PPPoE microservice (pppoed) manages PPPoE and PPP sessions.
IP-over-Ethernet (IPoE) is an alternative to PPPoE to deliver network access services to broadband subscribers. IPoE does not require client dial-in software and is easy to use when accessing the network. In RBFS, the IPoE microservice (ipoed) manages IPoE services using DHCPv4 and DHCPv6.
The L2TPv2 microservice (l2tpd) is used for the L2TPv2 tunnel and session handling. L2TP is a Layer-3 tunneling protocol that initiates a tunnel between an L2TP access concentrator (LAC) and an L2TP network server (LNS). This enables Point-to-Point Protocol (PPP) link layer to be encapsulated and transferred across the internet.
Accounting
RBFS accounting is the process of tracking subscriber activities and network usage in a subscriber session for auditing and billing. Accounting tracks information such as subscriber identity, the number of packets and bytes transferred from and to the network, start and stop times of the sessions and so on. The accounting keeps track of resources used by the subscriber during the sessions. This includes the session time called time accounting and the number of packets and bytes transmitted during the session called volume accounting. In RBFS, accounting can be performed based on classes or types of services such as video, VoIP, and data.
Support for Lawful Interception
RBFS supports Lawful Interception (LI) to allow legal authorities to obtain communications network data for analysis or evidence. LI is a technique of intercepting certain user data streams tunneling the intercepted traffic to a mediation device with the data and only the users with appropriate credentials can access the intercepted data.
HTTP Redirect Service
RBFS HTTP Redirect service allows network service providers to intercept and redirect HTTP request traffic from subscribers to a designated captive portal instead of the original destination. This powerful service has a multitude of use cases, ranging from subscriber re-authentication to enforcing acceptance of network usage policies. It allows network service providers to re-authenticate subscribers when necessary and ensure that users explicitly accept network usage policies before accessing services. By implementing the RBFS HTTP Redirect Service, network service providers can efficiently manage user access and enforce compliance with network regulations and policies, ultimately enhancing the overall security and user experience within their network environment.
RBFS (Hierarchical) Quality of Service
RBFS Quality of Service (QoS) is a method of prioritizing network traffic for mission-critical applications and high-priority network services such as voice and video. It provides control over a variety of traffic types and ensures that critical data traffic gets sufficient network resources such as bandwidth.
RBFS can perform priority forwarding of data packets throughout the network. For this preferential forwarding, it identifies and classifies the network traffic. So that the critical network packets get sufficient resources. RBFS QoS ensures the required level of service and provides cost benefits to network providers by enabling them to use network resources efficiently.
RBFS also supports Hierarchical Quality of Service (HQoS), a mechanism that allows you to specify Quality of Service (QoS) behavior for different traffic classes. QoS allows classifying services such as voice and video, but using HQoS, you can apply QoS policies to different users, VLANs, logical interfaces, and so on. RBFS employs HQoS by using the mechanisms such as classifier, queuing, scheduler, policer, shaper, and remarking. HQoS provides a higher degree of granularity in traffic management.
RBFS Carrier-Grade Network Address Translation
RBFS is multi-service edge routing software with which you can deliver both CGNAT and BNG functionalities on a single open switch to reduce costs and increase efficiency.
The RBFS CGNAT or NAT444 solution supports Network Address Port Translation (NAPT), which has the potential to conserve IPv4 addresses for service providers. NAPT is an effective method for allowing multiple devices to connect to the Internet using a single public IPv4 address.
The solution can address the IPv4 depletion challenge of service providers. Using the RBFS CGNAT, service providers can serve a large number of subscribers using a limited number of public IPv4 addresses.
RBFS CGNAT solution has some unique characteristics. Both BNG functionalities and CGNAT functionalities can coexist in a single RBFS device. RBFS CGNAT implements NAT in the chipset that allows for the delivery of CGNAT functionality in-line, fully integrated into the packet processing pipeline alongside other functions in the data plane itself, without requiring any additional chipset resources.
RBFS CGNAT supports deterministic NAT mode of address translation, which provides a consistent mapping of private IPv4 addresses with public IPv4 addresses and port ranges. This mode ensures a one-to-one mapping of private IPv4 addresses with public IPv4 addresses, allowing you to specify the private address and its matching public address and port range. The given private IPv4 address is always translated to the same public address.
Ethernet VPN - Virtual Private Wire Service
RBFS Ethernet VPN - Virtual Private Wire Service (EVPN-VPWS) technology provides point-to-point Layer 2 services over an IP or MPLS network. It is based on the EVPN (Ethernet VPN) technology, which extends the BGP (Border Gateway Protocol) to handle MAC addresses and Ethernet segments in addition to IP prefixes.
EVPN-VPWS allows service providers to offer Layer 2 services with better scalability, flexibility, and ease of operation compared to traditional Layer 2 technologies like VPLS (Virtual Private LAN Service). It uses BGP as the control plane protocol to distribute MAC reachability information across the network, enabling efficient MAC learning and forwarding.
RBFS Redundancy
RBFS supports deployment in redundancy mode that protects from link and node failures. Node and link outages that may occur on an RBFS access network can bring down the subscriber services. RBFS Redundancy helps to minimize the impact of these events and to reduce interruptions and downtime by providing a resilient system.
RBFS Redundancy protects subscriber services from various software and hardware outages. It provides mechanisms to enhance network resiliency that enables subscriber workloads to remain functional by ensuring a reliable switchover in the event of a node or link outage. With RBFS Redundancy, if one node goes down, another node can automatically take over the services.
RBFS Redundancy protects subscriber groups using an active standby node cluster model. RBFS Redundancy architecture consists of an active-standby node cluster and one node is active that runs workloads at a time. The peer node, which is identical to the first node, mirrors the concurrent subscriber state data from the peer and takes over workloads in the event of a node or link failure.
Zero Touch Provisioning
By leveraging the Zero Touch Provisioning (ZTP) feature, you can automate many of the RBFS deployment and setup tasks. ZTP allows you to set up and configure the platforms automatically by eliminating the repetitive manual tasks in a large-scale environment. This feature significantly reduces human touch points and errors prone by manual interventions and makes the deployment easier.
Scalability in RBFS
RBFS allows horizontal scaling to enhance system capacity. You can add additional switches to the spine and leaf layers to enhance capacity to handle increased subscriber traffic.
RBFS offers subscriber management capacity in a scale-out architecture called the Point-of-Deployment (PoD), also known as a SEBA PoD (SDN-enabled PoD). A large-scale PoD consists of access leaf routers aggregated by a layer of spine routers in an auto-provisioned CLOS topology. The access leaf routers provide subscriber management functionality. For even greater scalability, a layer of border leaf routers can be added to the core of the network provider network to provide more connectivity.
The leaf routers can be scaled out horizontally to increase the number of subscribers supported on the PoD, providing a pay-as-you-grow model. PPPoE subscribers can be terminated on the access leaf routers or tunneled to an LNS over L2TPv2. L2 Cross Connect (L2X) allows subscriber traffic to be tunneled out of the PoD at Layer 2, providing connectivity.
Security in RBFS
In RBFS, security is integrated into the foundation of the network. RBFS implements several techniques and methods to safeguard the entire network infrastructure. RBFS has a comprehensive set of security capabilities that deploy multiple security controls to protect different areas of the system and network.
Security features for RBFS Control Plane
RBFS Control Plane security feature enables filtering and rate-limiting the traffic transmitted from the forwarding plane to the control plane. RBFS uses Access Control Lists (ACLs) and policers to secure the router’s control plane.
All routing protocols, management protocols, and service protocols run in the control plane. The output of these protocols results in databases such as routing tables, MAC tables, ARP tables, and so on, which eventually get programmed in the forwarding plane.
ACLs are the building blocks of control-plane security. RBFS employs fundamental mechanisms - Protocol ACLs and Route Lookup - for redirecting control plane traffic to the CPU and policers for controlling CP traffic to the CPU.
All routing protocols (BGP, OSPF, and ISIS), Management Protocols (SSH, RESTCONF/YANG, and so on), Service Protocols (RADIUS, NTP, and TACACS+), and Access Protocols (PPPoE, DHCP, L2TP, and PPP) automatically create Access Control Lists (ACLs) required to punt the protocol traffic to the CPU Control Plane.
The RBFS Control Plane Security feature adds policers to all protocol ACLs. This feature creates a set of default policers and applies them to the protocol ACLs to secure the control plane from DDoS attacks.
Security features for RBFS Management Plane
RBFS provides the capability to restrict access to the management plane only to authenticated and authorized entities. The authentication identifies the entity and the authorization validates if the entity is allowed to execute the action.
RBFS supports the security protocol, TACACS (Terminal Access Controller Access Control System). RBFS provides a Pluggable Authentication Module (PAM) that enables it to work with TACACS for centralized authentication for users who try to access a router.
For management plane security, RBFS implements token-based authentication that provides access to the management plane through APIs only to the authenticated entities.
RBFS uses JSON web token, an open standard token, that defines a compact and self-contained way for securely transmitting information between parties as a JSON object. The ApiGwD microservice validates the access token against a JSON web key set (JKWS).
Logging and Observability in RBFS
RBFS logging is the process of writing log messages during the execution of an event. Logging provides reports about the events in the entire RBFS ecosystem at different functional areas. You can configure logging based on the different severity levels available. RBFS also allows you to send logs to third-party log management servers such as Graylog where you can view and analyze the real-time data. It provides you the ability to trace out the errors of the applications in real-time.
Operational state visibility is crucial for troubleshooting, testing, monitoring, and capacity management. To enable operational visibility, it is required to collect router metrics periodically. RBFS allows the ingestion of time-series data allows to send operational queries.
RBFS uses Prometheus, an open-source system monitoring and alerting tool, for monitoring and metric collection. Prometheus collects time-stamped data for events, network data, application performance, and so on. The tool allows analyzing metrics with the PromQL query language. Additionally, RBFS provides an optional alert management tool. You can use both of these tools together with its own services to integrate them into the RBFS ecosystem.
Observability Using SNMP
RBFS SNMP (Simple Network Management Protocol) provides a network monitoring mechanism that collects state information from various network devices and components. With SNMP, you can monitor interfaces, CPU usage, temperature of the device, bandwidth usage, and so on. For example, if an interface goes down on one of the devices, SNMP can quickly alert this. The RBFS SNMP implementation allows retrieving system state information using the Protocol Data Unit (PDU) from various network components.
SNMP allows performing various operations that include GET for retrieving data, SET for modifying data, TRAP for notifying an event and so on. These operations provide management access to the MIB hierarchy. RBFS supports the SNMP version 2c and SNMP version 3.
Resource Monitoring
Monitoring the device and its various components is very crucial to analyze the health of devices. RBFS provides resource monitoring capabilities to keep track of various components of the devices. RBFS has a dedicated microservice called resmond to discover and monitor the device resources. With RBFS Resource Monitoring, you can continuously observe the health of the system resources such as CPU, Memory, Processes, Disks, Sensor, and Optics.
RBFS Software Installation
RBFS software is available at RtBrick Image Store (https://releases.rtbrick.com/) where you can download the latest version. For more information on RBFS software installation, see RBFS Installation.