RADIUS Server Configuration
Subscriber Management often relies on the RADIUS server for authentication, authorization, and accounting. There are alternative AAA solutions, including local methods that operate independently of network availability.
The RADIUS server configuration is not standalone; it is inherently dependent on the configuration of a RADIUS profile. You must first create a RADIUS profile before configuring the associated RADIUS server.
The following diagram illustrates how RADIUS server configuration fits into the broader context of subscriber management tasks.
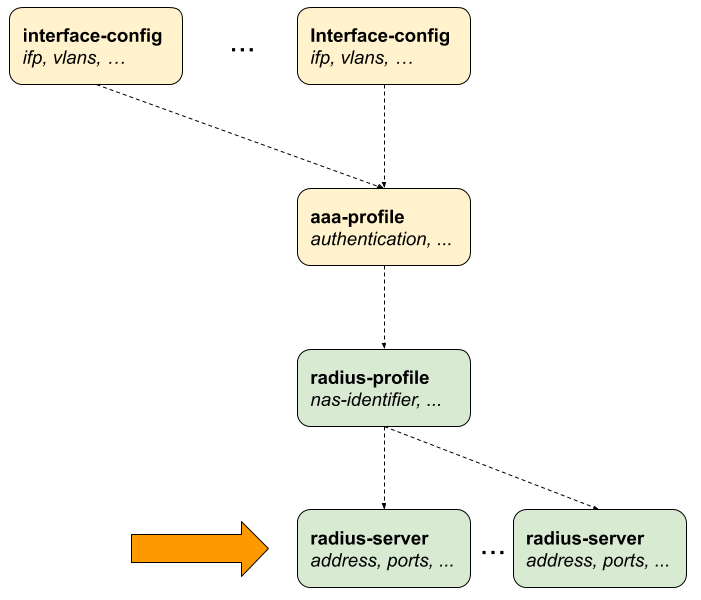
Configuring the RADIUS Server
The following configuration command and options are used to configure a RADIUS server.
supervisor@switch: cfg> set access radius-server <server-name> Name of the RADIUS server supervisor@switch: cfg> set access radius-server radius-server-1 <cr> accounting RADIUS accounting mode address RADIUS server address authentication RADIUS authentication mode coa RADIUS Change-of-Authorization (CoA) mode rate Maximum RADIUS requests per/second routing-instance Instance name secret-encrypted-text RADIUS secret in encrypted text secret-plain-text RADIUS secret in plain text source-address Source address used for RADIUS packets
The following example shows the RADIUS server configuration for authentication and accounting. Each of these options allows you to define how the RADIUS server will operate. The command sets RADIUS server name as ‘radius-server-1’. The configuration specifies the IP address '198.51.100.101' of the RADIUS server, which the router will use to send RADIUS requests. The source IP address is specified as '198.51.100.200'. It sets 'CoA' (Change-of-Authorization), a feature that allows the RADIUS server to change the authorization parameters of a session after it has been established.
The secret-encrypted-text parameter is specified that configures the RADIUS secret in an encrypted format. The key is used for encrypting RADIUS messages between the client and server to ensure security.
supervisor@switch: cfg> show config access radius-server radius-server-1
{
"rtbrick-config:radius-server": {
"server-name": "radius-server-1",
"address": "198.51.100.101",
"source-address": "198.51.100.200",
"secret-encrypted-text": "$21e4946e31b406de98b3077aef03ed5a7",
"authentication": {
"enable": "true"
},
"accounting": {
"enable": "true"
},
"coa": {
"enable": "true"
}
}
}
| Attribute | Description |
|---|---|
|
RADIUS server IPv4 address. Multiple RADIUS servers with the same IPv4 address are currently not supported, even if the instance or port is different.! |
|
Local source IPv4 address. |
|
The routing instance in which the RADIUS server is reachable. |
|
RADIUS secret, which can be provided as plaintext or already encrypted text. |
|
Maximum RADIUS requests per second. Default: 600 Range: 1 - 65535 |
 To access the RESTCONF API that corresponds to this CLI, click
here.
To access the RESTCONF API that corresponds to this CLI, click
here.
Configuring Authentication
The following command and options allow to configure the authentication settings on a RADIUS server. The enable option is used to activate RADIUS authentication for the specified RADIUS server 'radius-server-1'. The outstanding option allows you to specify the maximum number of pending authentication requests that the device can have at any given time. The port option enables you to define the port number used for RADIUS authentication requests. The retry option defines the maximum number of retries the device makes if the RADIUS server does not acknowledge an authentication request. This ensures that transient network issues do not cause authentication failures. The timeout setting determines the time, in seconds, that the device will wait for a response from the RADIUS server after sending authentication requests. If the server does not respond within this time frame, the request will be considered timed out.
supervisor@switch: cfg> set access radius-server radius-server-1 authentication <cr> enable Enable RADIUS authentication outstanding Maximum number of outstanding authentication requests port RADIUS server authentication port retry Maximum retries for authentication request packets timeout Authentication request timeout in seconds
| Attribute | Description |
|---|---|
|
Enables RADIUS authentication. Default: false |
|
RADIUS authentication port. Default: 1812 Range: 1 - 65535 |
|
This option specifies the number of authentication retries before declaring this server as unreachable for authentication. After reaching the limit, the client begins to send requests to other RADIUS servers and rejects the request after receiving the end of the list. Default: 3 Range: 1 - 255 |
|
Authentication request timeout, in seconds. Default: 5 Range: 1 - 65535 |
|
This option specifies the maximum number of outstanding authentication requests for this RADIUS server. A request is counted as outstanding if sent out but the response is not received. Default: 100 Range: 1 - 65535 |
 To access the RESTCONF API that corresponds to this CLI, click
here.
To access the RESTCONF API that corresponds to this CLI, click
here.
Configuring Accounting
RADIUS accounting allows the tracking of user sessions. This configuration sets up RADIUS accounting on a specified RADIUS server.
When enabled, the device will send accounting data to the RADIUS server.
supervisor@switch: cfg> set access radius-server radius-server-1 accounting <cr> enable Enable RADIUS accounting outstanding Maximum number of outstanding accounting requests port RADIUS server accounting port retry Maximum retries for accounting request packets timeout Accounting request timeout in seconds
| Attribute | Description |
|---|---|
|
Enable RADIUS accounting. Default: false |
|
This specifies the port number on the RADIUS server that is used for accounting purpose. Default: 1813 Range: 1 - 65535 |
|
This option determines the maximum number of attempts the device will make to send an accounting request to the RADIUS server before marking the server as unreachable for accounting. Once the retry limit is reached, the device will attempt to send accounting requests to other configured RADIUS servers. Default: 10 Range: 1 - 255 |
|
Accounting request timeout, in seconds. Default: 30 Range: 1 - 65535 |
|
This option specifies the maximum number of outstanding accounting requests for this RADIUS server. A request is counted as outstanding if sent out, but the response is not received. Default: 100 Range: 1 - 65535 |
 To access the RESTCONF API that corresponds to this CLI, click
here.
To access the RESTCONF API that corresponds to this CLI, click
here.
Configuring Change-of-Authorization (CoA)
Change-of-Authorization (CoA) allows a RADIUS server to send requests to the network device to change the authorization parameters of an active session. The following configuration involves setting up CoA for a specified RADIUS server called 'radius-server-1'.
supervisor@switch: cfg> set access radius-server radius-server-1 coa <cr> enable Enable Change-of-Authorization (CoA) port Local RADIUS CoA port
| Attribute | Description |
|---|---|
|
This option enables the device to receive CoA requests from the specified RADIUS server. Default: false |
|
Specifies the device port that listens/receives for CoA requests from the RADIUS server. Default: 3799 Range: 1 - 65535 |
 To access the RESTCONF API that corresponds to this CLI, click
here.
To access the RESTCONF API that corresponds to this CLI, click
here.