Access Profile Configuration
You must configure an access interface with an access profile name, such as pppoe-dual
and it is also essential to configure the properties and parameters of the access profile itself.
The following image illustrates the access interface configurations and how they are associated with the entire subscriber management configurations.
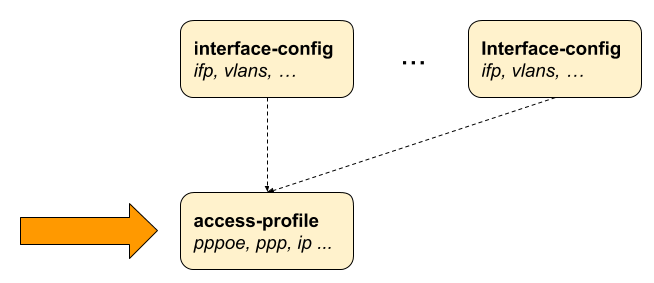
Configuring the Access Profile
Configuring an access profile involves specifying its name and defining various parameters to control how it handles network traffic and client interactions. The following command and options allow you to configure an access profile.
supervisor@switch: cfg> set access access-profile <profile-name> Name of the access profile supervisor@switch: cfg> set access access-profile pppoe-dual <cr> address-family Address-family configuration instance Instance name protocol Protocol configuration
The following table provides the command options/attributes and descriptions.
| Attribute | Description |
|---|---|
|
Change routing instance. Default: default |
PPPoE with IPv4 and IPv6
The following access profile configuration is for a PPPoE access profile named pppoe-dual that supports both IPv4 and IPv6. The instance is marked as default, and the session protection is enabled for PPPoE by setting the value to true, and the VLAN priority is set to 6.
The configuration defines various PPP parameters such as LCP, IPCP, and so on. For LCP (Link Control Protocol), the authentication protocol is specified as PAP_CHAP, indicating that both PAP (Password Authentication Protocol) and CHAP (Challenge Handshake Authentication Protocol) are allowed. The echo-interval, which is the interval in seconds for sending LCP echo requests to check the connection, is specified as 30 seconds. The echo-max-retransmit parameter, which is the maximum number of retransmissions for LCP echo requests before considering the link down, is set to 3. The configuration enables the LCP echo requests by specifying true for the echo-enable parameter.
In the configuration, both the IPCP and IP6CP are enabled by setting their values to true. These protocols are used to configure both the IPv4 and IPv6 settings over PPP. The source IFL (logical interface) for IPCP is specified as 'lo-0/0/0/1'. The RA (Router Advertisement) Configuration is enabled by setting the value to 'true', which allows the router to send RA messages for IPv6 configuration. The interval period for the RA messages is set to 60 seconds. DHCPv6 is enabled by setting the value to true, which allows the device to assign IPv6 addresses to the subscribers through DHCP.
The L2TP tunnel profile is defined as l2tp-default, which allows the encapsulation of PPP sessions over IP networks. Both IPv4 and IPv6 address families are enabled by setting their values to true using the address family configurations. For IPv4, the primary DNS server is specified '198.51.100.1' and the secondary DNS server is specified '198.51.100.4'. For IPv6, the primary DNS server is specified as '2001:db8:0:100::'' and the secondary DNS server is specified '2001:db8:0:104::'.
supervisor@switch: cfg> show config access access-profile pppoe-dual
{
"rtbrick-config:access-profile": {
"profile-name": "pppoe-dual",
"instance": "default",
"protocol": {
"pppoe": {
"enable": "true",
"session-protection": {
"enable": "true"
},
"vlan-priority": 6
},
"ppp": {
"lcp": {
"authentication-protocol": "PAP_CHAP",
"echo-interval": 30,
"echo-max-retransmit": 3,
"echo-enable": "true"
},
"ipcp": {
"enable": "true",
"source-ifl": "lo-0/0/0/1"
},
"ip6cp": {
"enable": "true"
}
},
"ra": {
"enable": "true",
"interval": 60
},
"dhcpv6": {
"enable": "true"
},
"l2tp": {
"tunnel-profile": "l2tp-default"
}
},
"address-family": {
"ipv4": {
"enable": "true",
"primary-dns": "198.51.100.1",
"secondary-dns": "198.51.100.4"
},
"ipv6": {
"enable": "true",
"primary-dns": "2001:db8:0:100::",
"secondary-dns": "2001:db8:0:104::"
}
}
}
}
IPoE with IPv4 and IPv6
The example configuration below sets up an IPoE access profile named 'ipoe-dual' to handle IPoE sessions, which support both IPv4 and IPv6 address families. The router acts as a DHCP server for both protocols, assigning IP addresses and DNS server information to client devices.
The profile name is ipoe-dual. By setting the value to true, this profile enables both DHCP and DHCPv6 protocols. The mode is defined as server for both DHCP and DHCPv6, which allows the router to act as a server for IPv4 and IPv6. The IPv4 address family is configured for the access profile by setting the value to true. For IPv4, proxy ARP is enabled by setting proxy-arp-enable to true.
The IPv4 address family is configured for the access profile by setting the value to ‘true. For IPv4, proxy ARP is enabled by setting proxy-arp-enable to true. This allows the router to respond to ARP requests on behalf of other hosts.
The pool name ipoe indicates the IPv4 address allocation to client devices. The primary DNS server for IPv4 is set to '198.51.100.1', and the secondary DNS server is specified as '198.51.100.4'.
The configuration includes various parameters for IPv6. The IPv6 pool name is ipoe-ia-na, which provides IPv6 addresses to subscribers. The prefix-delegation-pool-name parameter is set as ipoe-ia-pd for IPv6 prefix delegation. The primary and secondary DNS servers for IPv6 are specified as '2001:db8:0:100::' and '2001:db8:0:104::' respectively.
supervisor@switch: cfg> show config access access-profile ipoe-dual
{
"rtbrick-config:access-profile":{
"profile-name":"ipoe",
"protocol":{
"dhcp":{
"enable":"true",
"mode":"server"
},
"dhcpv6":{
"enable":"true",
"mode":"server"
}
},
"address-family":{
"ipv4":{
"enable":"true",
"proxy-arp-enable": "true",
"pool-name":"ipoe",
"primary-dns":"198.51.100.1,
"secondary-dns":"198.51.100.4"
},
"ipv6":{
"enable":"true",
"pool-name":"ipoe-ia-na",
"prefix-delegation-pool-name":"ipoe-ia-pd",
"primary-dns": "2001:db8:0:100::",
"secondary-dns": "2001:db8:0:104::"
}
}
}
}
Unrestricted Proxy-ARP Support for Subscriber IFLs
A configuration option is available for subscriber IFL to enable the unrestricted proxy-ARP to reply to all ARP requests from subscribers with the MAC address of the corresponding subscriber IFL.
Syntax:
Sample command:
set access access-profile access-profile1 address-family ipv4 proxy-arp any
Example:
supervisor@rtbrick: cfg> show config access access-profile access-profile1
{
"rtbrick-config:access-profile": [
{
"profile-name": "access-profile1",
"protocol": {
"ra": {
"enable": "true"
},
"dhcp": {
"enable": "true",
"mode": "server"
},
"dhcpv6": {
"enable": "true",
"mode": "server"
}
},
"address-family": {
"ipv4": {
"enable": "true",
"pool-name": "pool1",
"proxy-arp": "any"
},
"ipv6": {
"enable": "true",
"pool-name": "pool1",
"prefix-delegation-pool-name": "pool2",
"primary-dns": "1::1"
}
}
}
]
}
 To access the RESTCONF API that corresponds to this CLI, click
here.
To access the RESTCONF API that corresponds to this CLI, click
here.
Configuring IPv4
To make IPv4 available for access protocols such as PPP (PPPoE) or DHCP (IPoE), you must explicitly enable the IPv4 address family within the access profile.
supervisor@switch: cfg> set access access-profile pppoe-dual address-family ipv4 <cr> enable Enable IPv4 pool-name Local IPv4 pool name primary-dns Primary DNS server proxy-arp-enable Enable Proxy ARP secondary-dns Secondary DNS server static-ipv4 Static address
The following table provides the command options/attributes and descriptions.
| Attribute | Description | ||
|---|---|---|---|
|
Enable IPv4 Default: false |
||
|
The |
||
|
The primary DNS and secondary DNS servers configured are used by protocols such as PPP (PPPoE) or DHCP (IPoE) and advertised to the client. |
||
|
Enable (or disable) proxy ARP support for IPoE subscribers. Default: NONE. |
||
|
The
|
 To access the RESTCONF API that corresponds to this CLI, click
here.
To access the RESTCONF API that corresponds to this CLI, click
here.
Configuring IPv6
To make IPv6 available for access protocols such as PPP (PPPoE) or DHCP (IPoE), you must explicitly enable the IPv4 address family within the access profile.
supervisor@switch: cfg> set access access-profile pppoe-dual address-family ipv6 <cr> enable Enable IPv6 pool-name Local IPv6 pool name prefix-delegation-pool-name Local IPv6 prefix delegation pool name primary-dns Primary DNS server secondary-dns Secondary DNS server
The following table provides the command options/attributes and descriptions.
| Attribute | Description |
|---|---|
|
Enable IPv6 Default: false |
prefix-delegation-pool-name |
The |
|
The primary DNS and secondary DNS servers configured are used by protocols such as ICMPv6 router advertisements or DHCPv6 and advertise to the client. |
 To access the RESTCONF API that corresponds to this CLI, click
here.
To access the RESTCONF API that corresponds to this CLI, click
here.
Enabling IPv6 Router Advertisement
IPv6 Router Advertisement (RA) is a component of the IPv6 Neighbor Discovery Protocol (NDP). It is used by routers to broadcast their availability and provide various network parameters to devices that support IPv6 on the network. Enabling Router Advertisement is crucial for the automatic configuration of IPv6 addresses and other settings on IPv6-enabled devices.
supervisor@switch: cfg> set access access-profile pppoe-dual protocol ra <cr> enable Enable IPv6 router-advertisement interval Interval lifetime Lifetime preferred-lifetime Preferred lifetime
The following table provides the command options/attributes and descriptions.
| Attribute | Description |
|---|---|
|
Enable IPv6 router advertisement. Default: false |
|
IPv6 router advertisements interval in seconds. Sets the interval at which the Router Advertisement messages are sent. Default: 0 (disabled) |
|
The valid lifetime for the prefix in seconds. Default: 14400 |
|
The preferred lifetime for the prefix in seconds. Default: 1800 |
Configuring DHCPv4
To enable and configure DHCPv4 on the access profile, use the following command. This setup allows the access profile to handle DHCP requests and provide IP addresses to clients.
supervisor@switch: cfg> set access access-profile ipoe-dual protocol dhcp <cr> enable Enable DHCP lease-time DHCP lease time in seconds mode DHCP mode
The following table provides the command options/attributes and descriptions.
| Attribute | Description |
|---|---|
|
Enable DHCP. Default: false |
|
This option specifies the DHCP mode for handling DHCP requests. Default: server Values: server and relay |
|
Define the duration of IP address leases, in seconds. Default: 300 |
|
Configure global DHCP server. |
 To access the RESTCONF API that corresponds to this CLI, click
here.
To access the RESTCONF API that corresponds to this CLI, click
here.
Configuring DHCPv6
To configure DHCPv6 on an access profile, use the following command. This setup enables DHCPv6 functionality, prefix lifetimes, and the operating mode.
supervisor@switch: cfg> set access access-profile pppoe-dual protocol dhcpv6 <cr> enable Enable DHCPv6 lifetime Lifetime preferred-lifetime Preferred lifetime mode DHCPv6 mode
The following table provides the command options/attributes and descriptions.
| Attribute | Description |
|---|---|
|
Enable DHCPv6. Default: false |
|
This option defines the DHCPv6 mode where the server handles DHCPv6 requests locally and relay/proxy forwards those to the configured servers. The difference between relay and proxy is that proxy can hide the actual DHCPv6 server. Default: server Values: server and relay |
|
The duration for which the advertised prefix is valid. This is the total time the prefix remains usable before it needs to be renewed. Set this to the desired lifetime in seconds. Default: 14400 |
|
Set the lifetime for IPv6 prefixes, in seconds. It defines the duration during which the prefix is preferred for use. It should be less than or equal to the lifetime. If set higher than the lifetime, it will be adjusted to match the lifetime. The values for T1 and T2 are 0.5 and 0.8 times the shortest preferred lifetime. Default: 1800 |
|
Configure DHCPv6 server. |
 To access the RESTCONF API that corresponds to this CLI, click
here.
To access the RESTCONF API that corresponds to this CLI, click
here.
Configuring PPPoE and PPP
The PPPoE protocol must be explicitly enabled in the access profile to allow PPPoE sessions.
supervisor@switch: cfg> set access access-profile pppoe-dual protocol pppoe enable true
PPPoE
The PPPoE configuration allows changing the default behavior of the PPPoE protocol.
supervisor@switch: cfg> set access access-profile pppoe-dual protocol pppoe <cr> enable Enable PPPoE max-outstanding Maximum outstanding PPPoE sessions session-protection PPPoE session protection
The following table provides the command options/attributes and descriptions.
| Attribute | Description |
|---|---|
|
Enable PPPoE. Default: false |
|
Maximum outstanding PPPoE sessions. Default: 64 Range: 1 - 65535 |
When PPPoE session protection is enabled, any short-lived or failed sessions are logged. By default, a session that does not remain established for at least 60 seconds (min-uptime) is classified as a failed or short-lived session. Such failures trigger a block on new sessions for this IFP, VLAN, and MAC for one second (min-lockout) by default. With each subsequent failed session, the lockout duration increases exponentially until it reaches a maximum of 300 seconds (max-lockout). If no failed sessions occur for 900 seconds, the lockout interval is reset (currently, not configurable).
PPPoE session protection also logs the last subscriber ID and terminates the session with a code that indicates the reason for the failure.
supervisor@switch: cfg> set access access-profile pppoe-dual protocol pppoe session-protection <cr> enable Enable PPPoE session protection max-lockout Session protection maximum lockout time in seconds min-lockout Session protection minimum lockout time in seconds min-uptime Session protection minimum uptime in seconds
| Attribute | Description |
|---|---|
|
Enables PPPoE session protection. Default: false |
|
Session protection minimum lockout time (in seconds). Default: 1 |
|
Session protection maximum lockout time (in seconds). Default: 300 |
|
Session with an uptime less than this will trigger protection (in seconds). Default: 60 |
 To access the RESTCONF API that corresponds to this CLI, click
here.
To access the RESTCONF API that corresponds to this CLI, click
here.
Configuring PPP LCP
The PPP Link Control Protocol (LCP) configuration allows changing the default behavior of the LCP protocol.
supervisor@switch: cfg> set access access-profile pppoe-dual protocol ppp lcp <cr> authentication-protocol Authentication protocol config-nak-max Max configure-reject/nak [Range: <1-255>] echo-enable Enable echo requests echo-interval Echo interval in seconds [Range: <1-255>] echo-max-retransmit Echo maximum retries [Range: <1-255>] lcp-loop-detection Loop detection mru Maximum local MRU [Range: <1280-1500>] mru-negotiation MRU negotiation mtu Maximum local MTU [Range: <1280-1500>] retransmit-interval Retransmit interval in seconds [Range: <1-255>] retransmit-max Maximum retries [Range: <1-255>]
The following table provides the command options/attributes and descriptions.
| Attribute | Description |
|---|---|
|
This option allows you to specify the authentication protocol used during the LCP negotiation phase. By default, PPP authentication is set to Default: PAP_CHAP |
|
By default, RBFS responds to LCP echo requests but does not initiate them unless Default: true |
|
LCP echo request interval in seconds. Default: 30 Range: 1 - 255 |
|
LCP echo request retransmissions. Default: 3 Range: 1 - 255 |
|
Negotiate MRU Default: true |
|
Maximum local MRU (peer MTU) Default: 1492 Range: 1280 - 1500 |
|
Maximum local MTU (peer MRU) Default: 1492 Range: 1280 - 1500 |
|
This is used during the PPP connection process to detect and prevent loops in the network. It is achieved through the negotiation and validation of 'magic numbers'. Magic numbers are unique values used by both ends of a PPP connection to ensure that the data sent is not simply being looped back from the other end. By default, the negotiation and validation of magic numbers are enabled, providing protection against looping connections. You can disable loop detection by setting Default: true |
|
The LCP request retransmission interval. Default: 5 Range: 1 - 255 |
|
The LCP requests retransmission before the session is terminated if no response is received. Default: 3 Range: 1 - 255 |
|
The option Default: 16 Range: 1 - 255 |
 To access the RESTCONF API that corresponds to this CLI, click
here.
To access the RESTCONF API that corresponds to this CLI, click
here.
Configuring PPP IPCP
To enable IPv4 over PPPoE, both the address-family IPv4 and the protocol PPP IPCP must be explicitly enabled in the access profile. Additionally, the source-ifl option is a mandatory configuration that specifies the logical interface from which the local IPv4 address will be derived.
supervisor@switch: cfg> set access access-profile pppoe-dual protocol ppp ipcp <cr> config-nak-max Max configure-reject/nak [Range: <1-255>] enable Enable PPP IPCP passive Passive mode retransmit-interval Retransmit interval in seconds [Range: <1-255>] retransmit-max Maximum retries [Range: <1-255>] source-ifl Source IFL
The following table provides the command options/attributes and descriptions.
| Attribute | Description |
|---|---|
|
Enable IPCP Default: false |
|
IPCP passive mode Default: false |
|
This setting is required and should be set to obtain the local IPv4 address from a specific logical interface. It should be configured to use the loopback interface of the corresponding routing instance. If a |
|
The IPCP request retransmission interval. Default: 5 Range: 1 - 255 |
|
The IPCP requests retransmission before the session is terminated if no response is received. Default: 8 Range: 1 - 255 |
|
The option config-nak-max defines the maximum PPP IPCP configuration reject/nak messages that can be sent or received before the session is terminated. Default: 8 Range: 1 - 255 |
 To access the RESTCONF API that corresponds to this CLI, click
here.
To access the RESTCONF API that corresponds to this CLI, click
here.
Configuring PPP IP6CP
To use IPv6 over PPPoE, you must explicitly enable both the IPv6 address family and the PPP IP6CP protocol.
The following command demonstrates how to enable PPP IP6CP in the pppoe-dual access profile.
supervisor@switch: cfg> set access access-profile pppoe-dual protocol ppp ip6cp <cr> config-nak-max Max configure-reject/nak [Range: <1-255>] enable Enable PPP IP6CP passive Passive mode retransmit-interval Retransmit interval in seconds [Range: <1-255>] retransmit-max Maximum retries [Range: <1-255>]
The following table provides the command options/attributes and descriptions.
| Attribute | Description |
|---|---|
|
Enable IP6CP. Default: false |
|
IP6CP passive mode. Default: false |
|
This option sets the interval, in seconds, between retransmissions, for IP6CP requests. Default: 5 Range: 1 - 255 |
|
This option sets the maximum number of retransmission attempts. The IP6CP requests retransmission before the session is terminated if no response is received. Default: 8 Range: 1 - 255 |
|
The option defines the maximum PPP IP6CP configuration Default: 6 Range: 1 - 255 |
 To access the RESTCONF API that corresponds to this CLI, click
here.
To access the RESTCONF API that corresponds to this CLI, click
here.
Retention Timer for Subscriber Termination History Configuration
You can configure a retention period (in hours) for storing the termination history of access subscribers after they have been disconnected.
Syntax:
set access terminate-history-timeout <value>
| Option | Description |
|---|---|
<value> |
Specify the period of time (in hours). Range: 0 - 720. If '0' is specified, the data is not retained. |
Example:
set access terminate-history-timeout 10
{
"rtbrick-config:access": {
"terminate-history-timeout": 10
}
}