Test AAA
The test AAA subscriber feature allows operators to verify and test authentication and accounting (e.g. local or RADIUS) by emulating a subscriber without the need for external clients to be connected. This is a commonly used feature used during troubleshooting or to validate the RADIUS configuration.
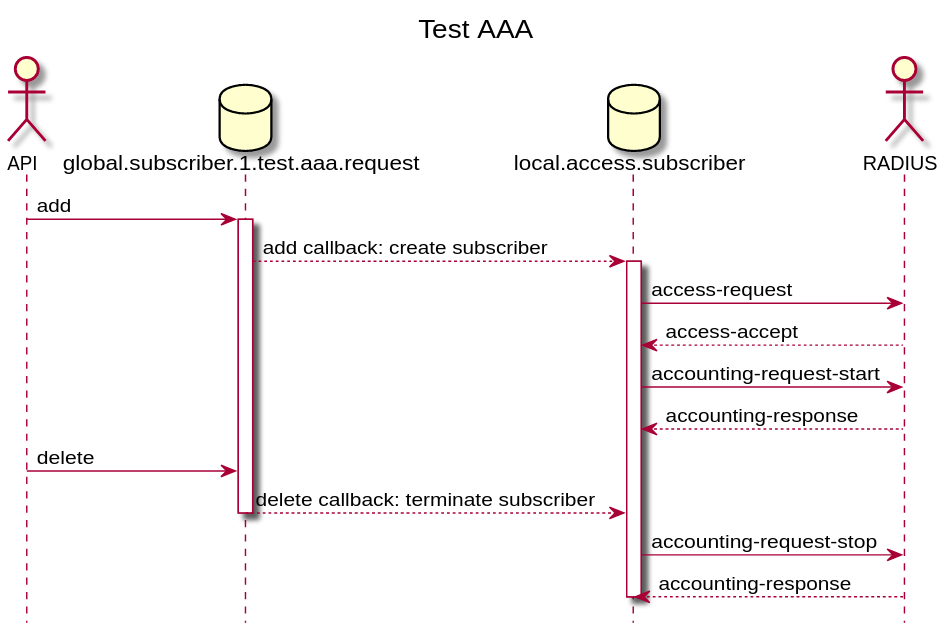
Test subscribers will be created by adding a request object into the test aaa request table (global.subscriber.1.test.aaa.request) via API or CLI. This request object includes beside username and password also a spoofed interface, outer-vlan, inner-vlan and MAC address required to build corresponding attributes like NAS port identifiers or the vendor specific RtBrick-Access-Stack. It is also possible to add an Agent-Circuit-Id or Agent-Remote-Id to test line based authentication.
This new object will first trigger a validation plugin to reject invalid requests (e.g. subscriber-id out of range, missing mandatory attributes, …). The add callback for this object will trigger the creation of the actual subscriber. Deleting the request object will trigger the termination of the subscriber. If this subscriber terminates for other reasons like CoA or CLI, the subscriber remains in a terminated state until the request object is deleted.
Compared to real subscribers, test subscribers will not trigger any forwarding state. Therefore no object will be created in the following tables for those subscribers:
-
global.access.1.subscriber.ifl
But the following tables will be populated for operators to check dynamic QoS, filters or IGMP:
-
global.access.1.subscriber.qos
-
global.access.1.subscriber.qos.shaper
-
global.access.1.subscriber.filter
-
global.access.1.subscriber.igmp.service
Those entries are ignored internally as there is no matching subscriber interface (IFL) (global.access.1.subscriber.ifl). The only exception here is the filter table meaning that received filters (ADF) learned from RADIUS are installed in the ACL table and applied with the IP addresses of the test subscribers.
Test AAA Subscriber-Id:
In RBFS each subscriber is uniquely identified by subscriber-id which is a 64 bit number allocated in a distributed fashion by the application creating the subscriber (for example, pppoed for pppoe sessions). This uniqueness is achieved with the following format.
The first 8 bits are used to identify the application:
-
0x00 subscriberd
-
0x01 pppoed
-
0x02 l2tpd
The next 8 bits are used to identify the application sharding instance allocated (for example, pppoed.1, pppoed.2, and so on).
The remaining 48 bits are used to uniquely identify the subscriber, which theoretically allows up to 281474976710656 subscribers per application instance.
An emulated test subscriber needs also a subscriber-id.
----- * 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 * +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ * | app-id (0) | app-instance | reserved | * +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ * | subscriber * +-+-+-+-+ -----
Assuming subscriber daemon instance 1 (subscriberd.1), the valid range for test subscriber identifiers is between 281474976710656 and 281479271677951.
Min Subscriber-Id: 281474976710656 0000 0000 0000 0001 0000 0000 0000 0000 0000 0000 0000 0000 0000 0000 0000 0000 Max Subscriber-Id: 281479271677951 0000 0000 0000 0001 0000 0000 0000 0000 1111 1111 1111 1111 1111 1111 1111 1111
The subscriber identifier will be allocated manually by operators from this range which has the advantage to easier identify the subscriber created by request.
Test AAA RADIUS Flow:
Test AAA Attributes
| Attribute | Mandatory | API | CLI | Default |
|---|---|---|---|---|
Subscriber-Id |
Yes |
subscriber_id |
subscriber-id |
|
Access Profile |
Yes |
access_profile_name |
access-profile |
|
AAA Profile |
Yes |
aaa_profile_name |
aaa-profile |
|
Username |
No |
user_name |
username |
test |
Password |
No |
password |
password |
test |
Agent-Circuit-id |
No |
aci |
aci |
|
Agent-Remote-id |
No |
ari |
ari |
|
Interface (IFP) |
* |
interface_name |
interface |
ifp-0/0/0 |
Outer VLAN |
No |
outer_vlan |
outer-vlan |
0 |
Inner VLAN |
No |
inner_vlan |
inner-vlan |
0 |
MAC Address |
No |
client_mac |
** |
00:00:00:00:00:00 |
* The interface is mandatory via CLI but optional via API.
** The client MAC address is currently supported via API only.
Test AAA via CLI
Note: In CLI strings must not contain the ΓÇ£#ΓÇ¥ and therefore this is not permitted for username, aci or ari set via CLI. This limitation is valid for CLI only as subscribers created via API are allowed to use this the ΓÇ£#ΓÇ¥ in the mentioned strings.
Add Test Subscriber:
supervisor@leaf1: op> test subscriber aaa request 281474976710656 pppoe-dual aaa-default ifl-0/0/1 username user1@rtbrick.com aci "0.0.0.0/0.0.0.0 eth 0/0" ari DEU.RTBRICK.01
List All Test Subscribers:
supervisor@leaf1: op> show subscriber test Subscriber-Id Interface VLAN State Username 281474976710656 ifp-0/1/23 0:0 ESTABLISHED user1@rtbrick.com
Delete Test Subscriber:
supervisor@leaf1: op> test subscriber aaa delete 281474976710656
Test AAA via API
Add Test Subscriber:
{{rbfs_url}}/api/v1/rbfs/elements/{\{element}}/services/subscriberd.1/proxy/bds/object/add
{
"table": {
"table_name": "global.access.1.test.aaa.request"
},
"objects": [
{
"attribute": {
"subscriber_id": 281474976710658,
"aaa_profile_name": "aaa-default",
"access_profile_name": "pppoe-dual",
"user_name": "user@rtbrick.com",
"ari": "DEU.RTBRICK.01",
"aci": "0.0.0.0/0.0.0.0 eth 0/0"
}
}
]
}Delete Test Subscriber:
{{rbfs_url}}/api/v1/rbfs/elements/{\{element}}/services/subscriberd.1/proxy/bds/object/delete
{
"table": {
"table_name": "global.access.1.test.aaa.request"
},
"objects": [
{
"attribute": {
"subscriber_id": 281474976710658
}
}
]
}List All Test Subscribers:
{{rbfs_url}}/api/v1/rbfs/elements/{\{element}}/services/subscriberd.1/proxy/bds/table/walk
{
"table": {
"table_name": "global.access.1.test.aaa.request"
}
}