IS-IS Multiarea Networks
Module Introduction
Before you start the hands-on part of this module, you should load the appropriate configuration and verify that the testbed is up and running by executing the corresponding robot file:
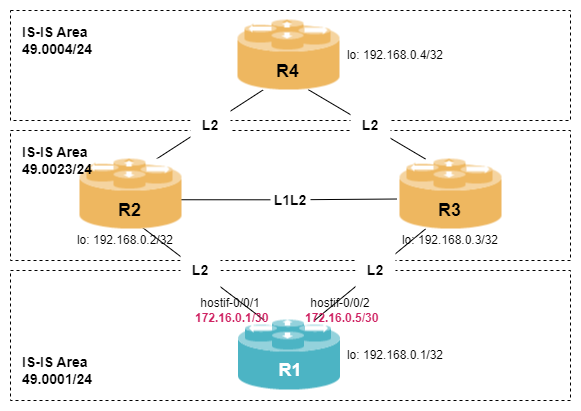
student@tour:~/trainings_resources/robot$ robot isis_multiarea/isis_multiarea_setup.robotIn order to get a better understanding, the lab setup is shown in the picture below.
Configuring IS-IS Level-2 Routing
In the previous module we restricted the IS-IS Routing to Level-1 only by disabling the Level-2 adjacencies on the corresponding interfaces. If you want to configure a Level-2 only router, you have to disable Level-1 adjacencies in a similar way.
R1 is part of IS-IS Area 49.0001. Please configure level-2 only adjacencies to R2 (hostif-0/0/1) and R3 (hostif-0/0/2). Also assign the loopback interface to this area. The authentication type is md5, the key-id1 is set to 2 and the password rtbrick.
Click to reveal the answer
cfg> set instance default protocol isis system-id 1921.6800.0001
cfg> set instance default protocol isis area 49.0001/24
cfg> set instance default protocol isis hostname R1
cfg> set instance default protocol isis router-id 192.168.0.1
cfg> set instance default protocol isis authentication level-2 type md5
cfg> set instance default protocol isis authentication level-2 key1-encrypted-text $21e4946e31b406de98b3077aef03ed5a7
cfg> set instance default protocol isis authentication level-2 key-id1 2
cfg> set instance default protocol isis interface hostif-0/0/1/0 level-1 adjacency-disable true
cfg> set instance default protocol isis interface hostif-0/0/2/0 level-1 adjacency-disable true
cfg> set instance default protocol isis interface lo-0/0/0/0 level-1 adjacency-disable true
cfg> commit
cfg> show isis neighbor
Instance: default
Interface System Level State Type Up since Expires
hostif-0/0/1/0 R2 L2 Up P2P Tue Apr 04 08:55:12 in 22s 835945us
hostif-0/0/2/0 R3 L2 Up P2P Tue Apr 04 08:55:16 in 26s 771878usAs R1 is now part of Level-2, it should have the full reachability information. Let’s take a look at the routing table for the loopback address of R4:
cfg> show route prefix 192.168.0.4/32
Instance: default, AFI: ipv4, SAFI: unicast
Prefix/Label Source Pref Next Hop Interface
192.168.0.4/32 isis 18 172.16.0.6 hostif-0/0/2/0
172.16.0.2 hostif-0/0/1/0From the output, we can see that R1 has two equally good paths to R4. The routing table does not provide any details about the metric. Remember, IS-IS is a link-state protocol preferring the path with the lowest metric. The routing table is populated by the IS-IS route table:
cfg> show isis route ipv4 unicast
Instance: default, AFI: ipv4, SAFI: unicast
Prefix Level Metric Type Next Hop Interface
172.16.0.0/30 2 1000000 Internal n/a local
172.16.0.4/30 2 1000000 Internal n/a local
172.16.0.8/30 2 1000100 Internal 172.16.0.2 hostif-0/0/1/0
172.16.0.12/30 2 1000100 Internal 172.16.0.6 hostif-0/0/2/0
172.16.0.2 hostif-0/0/1/0
172.16.0.16/30 2 1000100 Internal 172.16.0.6 hostif-0/0/2/0
192.168.0.1/32 2 1000000 Internal n/a local
192.168.0.2/32 2 1000010 Internal 172.16.0.2 hostif-0/0/1/0
192.168.0.3/32 2 1000010 Internal 172.16.0.6 hostif-0/0/2/0
192.168.0.4/32 2 1000110 Internal 172.16.0.6 hostif-0/0/2/0
172.16.0.2 hostif-0/0/1/0For the directly connected interfaces, IS-IS uses a default metric of 1000000. The total metric to reach 192.168.0.4/32 is 1000110. The metric can be modified on a per-interface and per-level basis using the syntax set instance <instance_name> protocol isis interface <ifl> <level> metric <metric>.
The IS-IS SPF calculation should result in two equally to node R4 (192.168.0.4/32). Configure the IS-IS interface metrics in such a way, that the path to R4 via R2 is preferred. However, the best path to R3 (192.168.0.3/32) should still be via the directly connected interface hostif-0/0/2.
Click to reveal the answer
The overall metric for the path R1-R2-R4 is currently 1000000+100+10=1000110 and for the path R1-R3-R4 also 1000000+100+10=1000110.
-
If we change the link metric for hostif-0/0/1 to 100, then metric(R1-R2-R4)=100+100+10=210. However, the metric(R1-R2-R3)=100+100+10 and metric(R1-R3)=1000000+10=1000010.
-
In order to achieve our goal, we need to adjust the metric for hostif-0/0/2 to a value bigger than 100 but lower than 200.
cfg> set instance default protocol isis interface hostif-0/0/1/0 level-2 metric 100
cfg> set instance default protocol isis interface hostif-0/0/2/0 level-2 metric 150
cfg> commit
cfg> show isis route ipv4 unicast
Instance: default, AFI: ipv4, SAFI: unicast
Prefix Level Metric Type Next Hop Interface
172.16.0.0/30 2 100 Internal n/a local
172.16.0.4/30 2 150 Internal n/a local
172.16.0.8/30 2 200 Internal 172.16.0.2 hostif-0/0/1/0
172.16.0.12/30 2 200 Internal 172.16.0.2 hostif-0/0/1/0
172.16.0.16/30 2 250 Internal 172.16.0.6 hostif-0/0/2/0
192.168.0.1/32 2 1000000 Internal n/a local
192.168.0.2/32 2 110 Internal 172.16.0.2 hostif-0/0/1/0
192.168.0.3/32 2 160 Internal 172.16.0.6 hostif-0/0/2/0
192.168.0.4/32 2 210 Internal 172.16.0.2 hostif-0/0/1/0IS-IS Level-1 and Level-2 Databases
The main reason for having multiple IS-IS levels is to reduce the size of the IS-IS database. While Level-2 routers maintain all link-state information in their database, Level-1 routers typically contain only link-state information for their local area. As a result, these routers require less memory and CPU resources to store and calculate SPF trees.
In contrast to OSPF, where ABR nodes inject default routes into areas to provide an exit into the backbone, IS-IS uses a different mechanism. An L1/L2 router with an active connection to the Level-2 network — meaning at least one active adjacency — sets the attached bit in its Level-1 LSP to indicate that it can act as a gateway out of the area.
Examining the output of the show isis database command, we can see separate entries for Level-1 and Level-2. In Level-1, only the local router R1 is present, since there are no Level-1 adjacencies. However, the Level-1 LSP shows the attached bit set, indicating that the router also participates in the IS-IS Level-2 backbone. In IS-IS, a Level-1 router receiving an LSP with the attached bit set automatically creates a default route.
cfg> show isis database
Instance: default, Level: 1
LSP ID Sequence Checksum Lifetime Overload Attached
R1.00-00 0x2 0x320 64153 0 1 (1)
Instance: default, Level: 2
LSP ID Sequence Checksum Lifetime Overload Attached
R1.00-00 0x2 0x3a73 64153 1 0
R2.00-00 0x6 0x6f40 64153 0 0
R3.00-00 0x6 0x970f 64153 0 0
R4.00-00 0x4 0x212 64130 0 0| 1 | Attached bit is bit set |
Inspecting R1’s Level-1 LSP in more detail, we see that it does not contain any reachability information, as no interfaces are assigned to Level-1 and no adjacencies exist.
cfg> show isis database level-1 node R1.00
Instance: default, Level: 1
LSP ID: R1.00-00
Interface:
LSP Header:
Sequence: 0x2
Checksum: 0x320
Remaining lifetime: 65535 seconds
Flags: Attached: 1, Overload: 0
Packet:
Length: 53 bytes
Last received time: 2025-12-04T08:57:19.601982+0000
Expiry: expires in 17h 47m 54s 703004us
System ID: 1921.6800.0001
Dynamic Hostname TLV (137): R1
Protocols Supported TLVs (129):
Network layer protocol ID: IPv6
Network layer protocol ID: IPv4
Area Address TLVs (1):
Area address: 49.0001In MPLS networks, it is often necessary to have more specific routes in Level-1 to establish MPLS LSPs. Although it is not required to include all individual backbone links in the Level-1 database, it is essential to have the loopback addresses of edge routers present for LSP signaling.
IS-IS provides a mechanism to selectively inject reachability information from Level-2 into Level-1. This process is known as route leaking. Since the primary purpose of introducing areas is to reduce database size, route leaking should be applied carefully.
On R1, create a policy that accepts all loopback IPv4 prefixes in the range 192.168.0.0/24, and apply this policy using the set instance default protocol isis level2-to-level1 route-leak command.
Click to reveal the answer
cfg> set policy statement LOOP_ONLY ordinal 1 match-logic and
cfg> set policy statement LOOP_ONLY ordinal 1 match rule 1 type ipv4-prefix
cfg> set policy statement LOOP_ONLY ordinal 1 match rule 1 value-type discrete
cfg> set policy statement LOOP_ONLY ordinal 1 match rule 1 match-type or-longer
cfg> set policy statement LOOP_ONLY ordinal 1 match rule 1 value 192.168.0.0/24
cfg> set policy statement LOOP_ONLY ordinal 1 match rule 2 type ipv4-prefix
cfg> set policy statement LOOP_ONLY ordinal 1 match rule 2 value-type discrete
cfg> set policy statement LOOP_ONLY ordinal 1 match rule 2 match-type prefix-length-exact
cfg> set policy statement LOOP_ONLY ordinal 1 match rule 2 value 0.0.0.0/32
cfg> set policy statement LOOP_ONLY ordinal 1 action rule 1 operation return-permit
cfg> set instance default protocol isis level2-to-level1 route-leak policy LOOP_ONLY
cfg> commitNow, let’s have another look at L1 LSP of R1:
cfg> show isis database level-1 node R1.00
Instance: default, Level: 1
LSP ID: R1.00-00
Interface:
LSP Header:
Sequence: 0x5
Checksum: 0x2f3
Remaining lifetime: 65535 seconds
Flags: Attached: 1, Overload: 0
Packet:
Length: 107 bytes
Last received time: 2025-12-04T09:50:17.203959+0000
Expiry: expires in 18h 12m 2s 479856us
System ID: 1921.6800.0001
Dynamic Hostname TLV (137): R1
Protocols Supported TLVs (129):
Network layer protocol ID: IPv6
Network layer protocol ID: IPv4
Area Address TLVs (1):
Area address: 49.0001
IPv4 Reachability TLVs (135):
IPv4 prefix: 192.168.0.1/32 Metric: 10 Internal Down (1)
IPv4 prefix: 192.168.0.2/32 Metric: 110 Internal Down (1)
IPv4 prefix: 192.168.0.3/32 Metric: 210 Internal Down (1)
IPv4 prefix: 192.168.0.4/32 Metric: 210 Internal Down (1)| 1 | Prefixes matching the policy have been leaked from Level-1 to Level-2. In additon the down bit is set to ensure, they are not sent back to the backbone. |
|
By default, a Level-1 router calculates the path to the closest Level-1/2 router with the attached bit set to send traffic towards the backbone. If sending traffic out of the local area is not desired, the Level-1 router can be configured to ignore the attached bit using the `set instance default protocol isis ignore-attached-bit true`command. |