Overview
The Securing Management Plane feature provides the capability to restrict the access to the management plane only to authenticated and authorized subjects.
The authentication identifies a subject, and the authorization validates if the subject is allowed to execute the action.
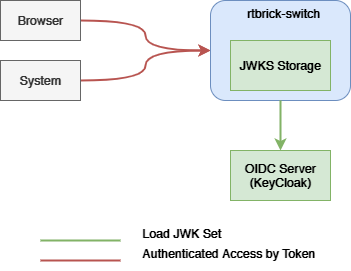
The figure-1 shows the data flow when accessing an rtbrick-switch. Each call against the switch in more detail against the API Gateway Daemon (APIGWD) of the switch has to be authenticated with an access token. There is only one exception when accessing the CTLRD’s UI; it is possible to be redirected to an OpenIDConnect Authenticator.
The APIGWD validates the access token against an JSON Web Key Set (JWKS) (https://tools.ietf.org/html/rfc7517). This key set can be loaded from a file locally on the system or auto discovered via the OpenIDConnect server.
A valid access token, in the sense of syntactically correct but also successfully validated signature by one of the JSON Web Key of the JWKS files, leads in an authenticated user. If the validation is unsuccessful, the call will be rejected.
The access token contains scopes which are used internally for the authorization checks. The authorization is a role based authorization where the scopes equal to the roles.
Internally the access token is converted to an RtBrick token, and all the communications inside the switch is authenticated via this RtBrick token.
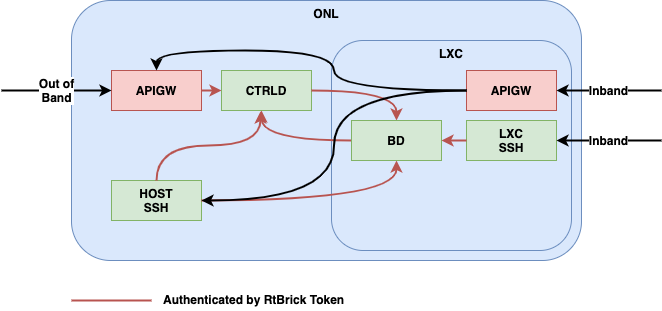
The dataflow inside of the switch can be seen in Figure 2.
The scopes of the access token are copied to the RtBrick Token.