SSH with TACACS+
RBFS provides a custom pluggable authentication module that gets invoked by the stock sshd on login. The necessary configurations are pre-installed on RBFS.
RtBrick-PAM, referred to as RTB-PAM helps in landing the TACACS authentication on the appropriate user in the Ubuntu container and helps in providing necessary details for the secure management plane feature.
Once the PAM client requests TACACS for the authentication, with successful authentication TACACS responds with a few RtBrick specific details.
{
rtb-deny-cmds: “clear bgp peer”
priv_lvl : some_level
}
On successful authentication, the RTB-PAM module creates a token (JWT) for the logged-in ssh user.
RTB-PAM Token
Token created by the RTB-PAM module contains the same claims that are defined under the RtBrick Token section, and this token is signed with the secret_jwks.json key.
The scope claim in the rtb-token is derived from the Linux groups that the locally mapped user belongs to.
The deny commands are converted into the claim rtb-deny-cmds. Once the token is created, it is transferred to the environment variable.
setenv RTB_TOKEN = {
"sub": "83692",
"iat": 1516239022,
"exp": 1517239022,
"name": "Admin User",
"preferred_username", "user1",
"scope": "operator tacacs_priv_lvl_8"
"rtb-deny-cmds": "^clear bgp peer"
}
After the RTB-PAM token is created, the CLI prompt appears. If a token is not created for the logged-in user, then the user cannot perform communication with the BD.
SSH User Prompt
After you successfully log into RBFS via SSH, you can see the rtb-token using the shell environment. For example, an SSH prompt may look like the example below.
rtbng@b908f71f63b7:~$ env SSH_CONNECTION=198.51.100.1 33136 198.51.100.44 22 LESSCLOSE=/usr/bin/lesspipe %s %s LANG=C.UTF-8 USER=rtbng PWD=/home/tacacs12 HOME=/home/tacacs12 SSH_CLIENT=198.51.100.1 33136 22 SUDO_USER=rtbng PRIV_LVL=1 SSH_TTY=/dev/pts/1 SUDO_PROMPT=[sudo] password for rtbng: MAIL=/var/mail/rtbng TERM=xterm-256color SHELL=/bin/bash SHLVL=1 LOGNAME=rtbng PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games LESSOPEN=| /usr/bin/lesspipe %s _=/usr/bin/env RTB_TOKEN=eyJhbGciOiJIUzI1NiIsImtpZCI6InJ0YnJpY2siLCJ0eXAiOiJKV1QifQ.eyJleHAiOjE0NTE2MDczMDAsImlhdCI6MTQ1MTYwNjQwMCwiaXNzIjoicnRicmljay1hcGktZ3ciLCJuYW1lIjoiQmhpc2htYSBBY2hhcnlhIiwicHJlZmVycmVkX3VzZXJuYW1lIjoiYmhpc2htYSIsInNjb3BlIjoic3lzdGVtIiwic3ViIjoiOTllOGI0YTEtM2E2Yi00YzI5LWJlZGItN2U3N2NjOTFjZTZiIn0.NOOAcafmHfgx-QFwiC-_VGokbvUwrTOjhfpD9px3hMY
| The users having access to the Linux shell only can see the installed rtb-token in the shell environment. |
User Login Flow
The figure below shows the user login flow.
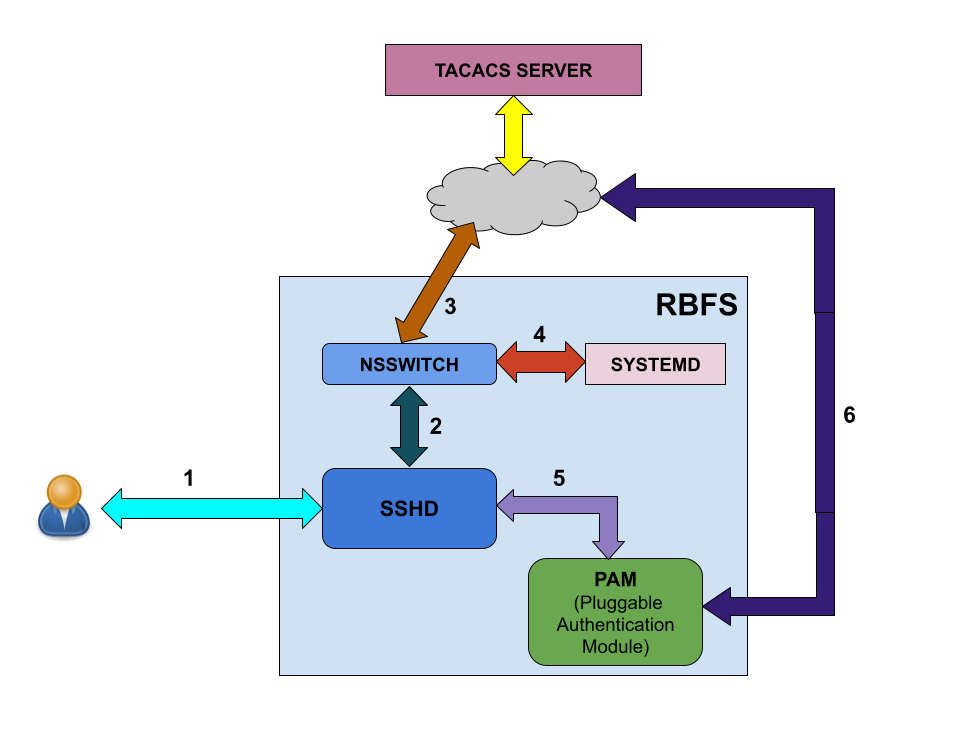
As shown in the figure above, the following steps are involved in the user login flow.
-
User starts to initialize using ssh
-
The SSH daemon (sshd) refers to the Name Service Switch (NSSWITCH) for user lookup
-
NSSWITCH performs a user lookup at the TACACS server
| A user lookup happens at TACACS user database even for the local users, except for the user 'supervisor'. |
-
If the user is not found at TACACS user database, then the user look up happens at the local user database.
-
User authentication is performed by PAM modules
-
PAM communicates to the TACACS server for authentication if it is a TACACS user
Linux pre-configured users and groups
| User Name | Group Name | Privilege |
|---|---|---|
supervisor |
supervisor |
level 15 |
operator |
operator |
level 7-14 |
reader |
reader |
level 0-6 |
In-Band and Out-of-Band TACACS user SSH Login
Configuring TACACS+ for RBFS
To configure TACACS+ server for RBFS, enter the the following commands.
Syntax
set system authorization tacacs server-ip <IP address> type <management type> secret-plain-text <secret key>
set system authorization tacacs server-ip <IP address> type <management type> server-port <server port number>
Command Arguments
| <IP Address> | IP address of the TACACS Server |
|---|---|
<management type> |
in-band or out-of-band management |
secret-plain-text> |
Secret plain text string. The secret string input can be plaintext format. If string starts with 1 then system considers it as encrypted string and stores key as it is. Also if secret string starts with 0, then system considers it as secret in plaintext and hence it stores in the system in encrypted format. |
<server port number> |
Server port number. This attribute is optional and by default system tries to connect to server running on port number 49. |
|
For TACACS login to work with inband management, inband configuration must be enabled with the following command: set inband-management instance <instance-name> tacacs true |
Example
root@rtbrick: cfg> set system authorization tacacs 198.51.100.111 out-of-band secret-plain-text testkey root@rtbrick: cfg> set system authorization tacacs server-ip 198.51.100.101 type inband server-port 1234
| A TACACS user is not allowed to login without TACACS server configuration. |
The example below shows the running configuration after you configure TACACS.
{
"rtbrick-config:system": {
"authorization": {
"tacacs": [
{
"ipv4-address": "198.51.100.111",
"type": "out-of-band",
"secret-encrypted-text": "$202a74ca845585855b6f8df57cdbf7858"
}
]
}
}
}
Example: TACACS User Configuration in the TACACS Server
The example below shows the server configurations for rtb-deny-cmds.
accounting file = /var/log/tac_plus.acct
key = tacacskey
user = bob {
login = cleartext "bob"
member = Network_Operator
}
group = Network_Operator {
default service = permit
service = exec {
priv-lvl = 10
rtb-deny-cmds = "show bgp.*"
}
}
priv-lvl is a mandatory attribute in the TACACS user configuration.
|
Multiple cmd-regexes can be configured with each regexes separated by semicolon (;).
Example:
rtb-deny-cmds = "show bgp .*;show isis .*"
Troubleshooting NSS User Lookup Issues
To look up the TACACS username with all NSS methods, enter the following command:
ubuntu@rtbrick:~$ sudo getent passwd <tac_user>
To look up the local user within the local user database, enter the following command:
ubuntu@rtbrick:~$ sudo getent -s compat passwd <local_user>
To look up the TACACS user within the TACACS+ server database, enter the following command:
ubuntu@batman:~/development$ sudo getent -s tacplus passwd <tacuser>
If TACACS does not appear to be working correctly, You can enable debug logging by adding the debug=1 parameter to one or more of these files:
/etc/tacplus_servers /etc/tacplus_nss.con
Configuring Secure Management Logs
SSH User Login Logs
The transaction logs of users (in the PAM module) are available in the following log file:
/var/log/auth.log
Commands to enable secure-management logging:
Full Syntax |
set log bd <bd_name> module secure_management logmap <log_map> level <log-level> |
Parameter descriptions |
|
Command modes |
|
Behavior description |
Enables secure-management logging in the system |
Example |
confd> set log bd all module secure_management logmap all level Info |