Securing the Control Plane Overview
Control plane security is essential for ensuring the reliable operation of a router by controlling the flow of traffic directed from the forwarding plane to the control plane. This protection is achieved primarily through filtering or rate-limiting mechanisms that prevent unwanted or potentially harmful traffic from overwhelming the router’s control functions. In RBFS, the control plane is secured by using Access Control Lists (ACLs) and policers, which are implemented and enforced on the forwarding plane. These ACLs and policers allow precise control over which packets are allowed to reach the control plane and at what rate, effectively safeguarding essential router processes from excessive load or attacks.
Furthermore, control plane security includes the capability to mark traffic generated by the control plane itself. This traffic marking facilitates prioritization within the network, enabling Quality of Service (QoS) benefits and allowing other network devices to identify and apply appropriate filtering or handling policies.
By combining filtering, rate-limiting, and traffic marking, RBFS provides a comprehensive framework to maintain the integrity, stability, and performance of the router’s control plane in complex network environments.
Control Plane Traffic
The control plane handles all routing, access, and management protocols. It processes information and configures it into the forwarding plane. For example, routes learned via protocols such as BGP and chosen by the route resolver are programmed into the forwarding plane.
An exception is the management protocols running on the out-of-band management port (typically named me0), which is directly linked to the control plane. Traffic received on this interface does not traverse the forwarding plane and thus is not protected by control plane security mechanisms. This separation ensures no forwarding between forwarding plane interfaces and the out-of-band management interface in the control plane.
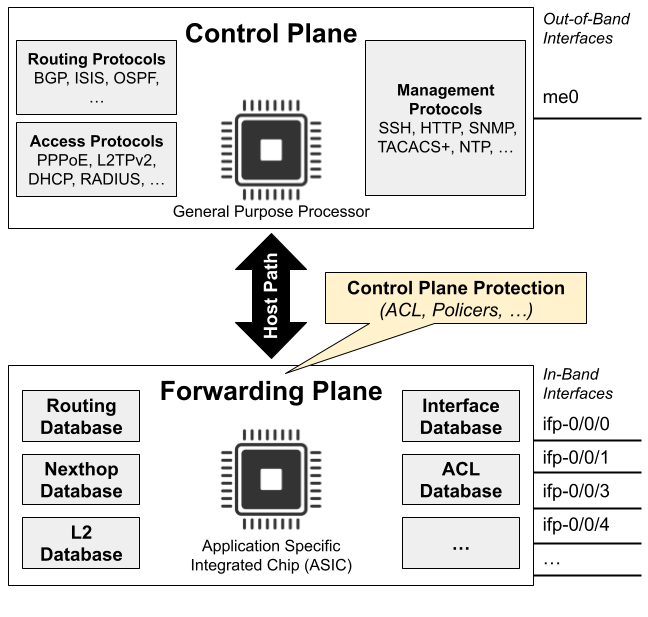
The diagram shows routing protocols (BGP, ISIS, OSPF), management protocols (SSH, HTTP, SNMP, TACACS+, NTP), and access protocols (PPPoE, L2TPv2, DHCP, RADIUS) associated with the control plane. The control plane uses general-purpose processors and builds databases like forwarding and ACL tables.
Conversely, the forwarding plane uses copies of these tables to make packet flow decisions based on match-action entries. The forwarding plane is implemented with high-performance ASICs capable of handling very high packet rates.
There are two kinds of traffic:
-
Control Traffic: Packets destined to the device itself, processed by the router CPU. These are identified by matching destination address, ACL rules, or exceptions (e.g. invalid fields, packet size, TTL).
-
Transit Traffic: Packets passing through the router, not destined to it, are forwarded via physical interfaces.
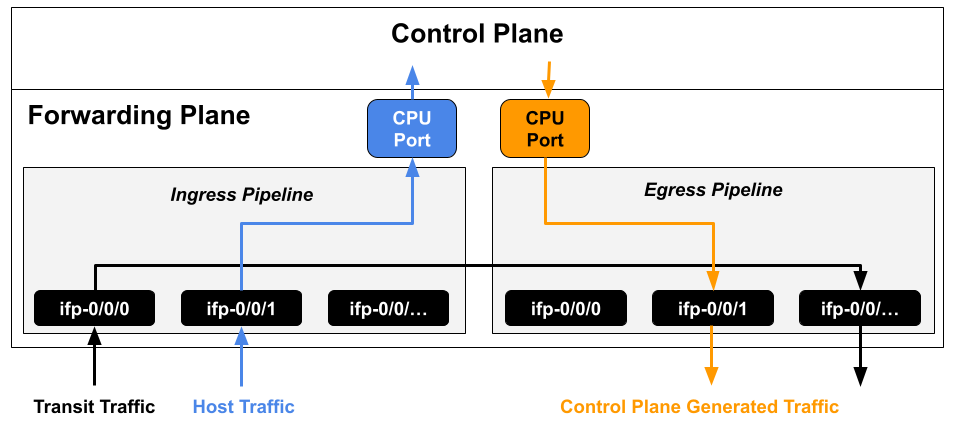
All control traffic is directed to CPU ports for processing by the control plane. Because general-purpose processors are not optimized for high packet rates, excessive control plane traffic (e.g. from an attacker) can overwhelm the router. Hence, controlling, filtering, and rate-limiting unwanted control-plane traffic is essential for protection.
Securing the Control Plane
In RBFS, control-plane traffic can be redirected to the CPU by three main mechanisms:
-
via ACLs
-
via route lookup
-
via exception (e.g. packet size, TTL)
All those mechanisms need to be considered and secured separately, as described in the following sections.
Control Plane Traffic via Protocol ACLs
Control plane security is built upon automatically generated Access Control Lists (ACLs) for enabled routing, management, and access protocols. These protocol ACLs direct their respective traffic to the control plane. Each ACL rule specifies match criteria and corresponding actions, such as redirecting traffic to the CPU and applying policers, when a packet matches.
Such protocol ACLs are also sometimes referred to as Trap.
|
Protocol ACLs:
-
auto-generated
-
specific (e.g. match IPv6 link-local neighbors)
-
high priority of 50 (lower values have priority over higher values)
-
can be verified with
show aclcommand -
do not require manual configuration
Example 1: Protocol ACL created by BGP
supervisor@rtbrick: op> show acl detail
<...>
Rule: default_bgp_l4_trap_192.0.2.101_192.0.2.102_dst
ACL type: l3v4
Ordinal: - Priority: 50
Match:
Direction: ingress
Destination IPv4 address: 192.0.2.102
Source IPv4 address: 192.0.2.101
Destination L4 port: 179
IP protocol: tcp
Action:
Redirect to CPU: True
Policer profile name: _DEFAULT_POLICER_50_MB
Result:
Trap ID: bgp
ACL Handle: 268
<...>
The default policer, _DEFAULT_POLICER_50_MB, restricts traffic on these ACLs to 50 Mbps. This bandwidth is shared across all protocols that reference this policer. While almost all protocols share the same policer by default, it is possible to configure dedicated policers for individual protocols or groups of protocols as described in the Control Plane Security Configuration section.
Control Plane Traffic via Route Lookup
By default, traffic sent to a router’s IP address (referred to as "my IP") that lacks an existing Access Control List (ACL) will be forwarded to the CPU via route lookup. This behavior applies to IP addresses configured on any interface, including loopback interfaces. To protect the control plane from malicious traffic targeting these IP addresses, user-defined ACL rules must be configured in RFBS. These are ACLs that are manually created by the user.
Configuring such ACLs to protect "my IP" is described in the Control Plane Security Configuration section.