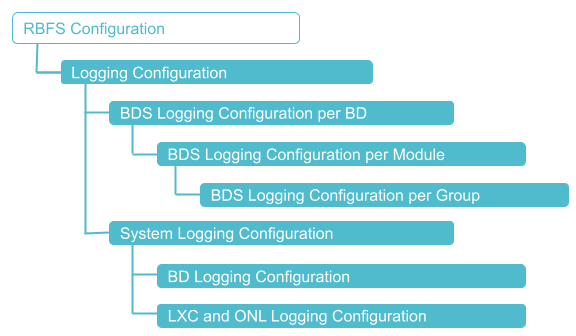
Logging Configuration
Configuration Overview
BDS (Brick Data Store) is an in-memory state database and a core component of RBFS. It stores all system state information as structured objects within its tables. Acting as a central communication hub across components, BDS generates a substantial volume of logs that are essential for monitoring.
You can enable logging for:
-
Brick Daemon (such as
pppod,ipod,confd, and so on) -
Modules (such as OSPF, BGP, ISIS, and so on)
-
Host (ONL) system
Once logs are generated, you view logs:
-
In the
varlog files -
Using operational commands
You can export the logs to an external server using the formats:
-
GELF
-
Syslog
Configuration Syntax and Commands
The following sections describe the logging configuration syntax and commands.
BDS Logging Configuration
You can configure BDS logging for a BD, a module, and for a group.
A specific configuration takes priority over a generic configuration. For example, if you have configured a global log level of bgp.iod.1 to "warning", and you have configured a log level of bgp module to "notice", then the final log level of bgp will be "notice".
|
Configuring BDS Logging for a Brick Daemon
You can configure BDS logging for a brick daemon or all daemons to generate logs related that daemon/daemons.
Syntax:
set log bd <bd-name> <option> …
| Attribute | Description |
|---|---|
<bd-name> |
Configure for the specified BD name. |
all |
Configure for all BDs. |
module <module-name> |
Module name. For more information, see the section "Configuring BDS Logging for a Module". |
plugin-alias alias-name <alias-name> |
Specify the external log management server name for sending the logs to the server. |
plugin-alias level <level> |
Log severity level. You can filter logs based on the log severity levels for sending to the external log management server. This allows to send only the required log messages to the log management server instead of sending a whole lot of data. For example, if you configure |
Example 1: BDS logging for a BD Configuration
{
"ietf-restconf:data": {
"rtbrick-config:system": {},
"rtbrick-config:log": {
"bd": [
{
"bd-name": "bgp.iod.1",
"level": "info",
"plugin-alias": {
"alias-name": "ztp",
"level": "error"
}
}
]
}
Configuring BDS Logging for a Module
You can enable logging for a module such as BGP, IS-IS, and so on.
Syntax:
set log module <module-name> <option> …
| Attribute | Description |
|---|---|
<module-name> |
Module name |
group <group-name> |
BDS log module log-group configuration. For more information, see the section "Configuring BDS Logging for a Group". |
level <level> |
Log severity level. |
plugin-alias alias-name <alias-name> |
Plugin alias name |
plugin-alias level <level> |
Log level. You can filter logs based on the log severity levels for sending to the log management server. This will help you to send only the required log messages to the log management server instead of sending a whole lot of data. For example, if you configure |
Example 1: Logging Module Configuration
{
"ietf-restconf:data": {
"rtbrick-config:system": {},
"rtbrick-config:log": {
"module": [
{
"module-name": "igmp",
"level": "info",
"plugin-alias": {
"alias-name": "graylog-srv1",
"level": "warning"
}
}
]
}
}
}
Configuring BDS Logging for a Group
You can enable logging for a group of log IDs. This configuration allows you to generate logs for a group of log IDs (also known as log maps). Using log groups, you can enable logging for a specific set of log IDs. This approach gives you more targeted control over log generation, helping you collect only the relevant information without overwhelming the system.
Syntax:
set log module <module-name> group <group-name> <option> …
| Attribute | Description |
|---|---|
<group-name> |
Group name |
level <level> |
Specifies the level of the plug-in alias. |
rate-limit <rate-limit> |
Rate-limiting is only supported for log groups. Configuring a higher rate-limit for a whole module may cause system instability due to generation of high volume of logs. The default value is 10. |
plugin-alias alias-name <alias-name> |
Plugin alias name |
plugin-alias level <level> |
Specifies the level of the plug-in alias. You can filter logs based on the log severity levels for sending to the log management server. This will help you to send only the required log messages to the log management server instead of sending a whole lot of data. For example, if you configure |
Example 1: Logging Group Configuration
{
"ietf-restconf:data": {
"rtbrick-config:log": {
"module": [
{
"module-name": "bgp",
"group": [
{
"group-name": "interface",
"level": "warning"
}
]
}
]
}
}
}
System Logging Configuration
LXC and ONL Logging Configuration
In addition to configuring logging for the various daemons and modules in RBFS container, you can also enable logging for the underlying ONL host syste. You can send logs from Linux and ONL system facilities such as auth, authpriv, daemon, and kern to the log management server.
Also, you can configure an external log management server to transport logs. Currently, Syslog and Graylog are the log management servers supported by RBFS.
Syntax:
set log system facility <facility-name> plugin-alias <attribute> <value>
| Attribute | Description |
|---|---|
<facility-name> |
Supported facilities include |
plugin-alias alias-name <alias-name> |
Plugin alias name |
plugin-alias level <level> |
Specify the level of the plug-in alias. You can filter logs based on the log severity levels for sending to the log management server. This will help you to send only the required log messages to the log management server instead of sending a whole lot of data. For example, if you configure |
Example 1: System Log Configuration
{
"ietf-restconf:data": {
"rtbrick-config:log": {
"system": {
"facility": [
{
"facility-name": "kern",
"plugin-alias": {
"alias-name": "graylog",
"level": "notice"
}
}
]
}
}
}
}
External Log Server (Plugin Alias) Configuration
You can configure an external log management server as a destination to send logs.
Syntax:
set system host log-alias <attribute> <value>
| Attribute | Description |
|---|---|
<name> |
Log alias name |
<address> |
Plugin address. For example, Gelf: http://11.1.1.1:1102/gelf Syslog: 10.1.1.1:8008 |
level |
Severity level for the log. |
network |
Log alias endpoint port. |
type |
Server type of log alias. |
Example 1: Log alias Configuration
set system host log-alias bng endpoint http://10.1.1.1:1102/gelf
set system host log-alias bng endpoint http://10.1.1.1:1102/gelf type gelf
set system host log-alias bng endpoint http://10.1.1.1:1102/gelf network http
set system host log-alias bng endpoint http://10.1.1.1:1102/gelf level info
{
"ietf-restconf:data": {
"rtbrick-config:system": {
"host": {
"log-alias": [
{
"name": "bng",
"endpoint": [
{
"address": "http://10.1.1.1:1102/gelf",
"type": "gelf",
"network": "http",
"level": "info"
}
]
}
]
}
}
}
}
This following configuration sets up how system logs will be exported to an external log collector, in this case, Graylog.
Example configuration for Graylog with the domain name:
set system set system host set system host log-alias graylog set system host log-alias graylog endpoint http://10.1.1.1:2002/gelf set system host log-alias graylog endpoint http://10.1.1.1:2002/gelf type gelf set system host log-alias graylog endpoint http://10.1.1.1:2002/gelf network http set system host log-alias graylog endpoint http://10.1.1.1:2002/gelf level info
{
"ietf-restconf:data": {
"rtbrick-config:system": {
"host": {
"log-alias": [
{
"name": "graylog",
"endpoint": [
{
"address": "http://10.1.1.1:2002/gelf",
"type": "gelf",
"network": "http",
"level": "info"
}
]
}
]
}
}
}
}
Example for Syslog configuration with TCP:
set system set system host set system host log-alias syslog set system host log-alias syslog endpoint 10.200.32.49:525 set system host log-alias syslog endpoint 10.200.32.49:525 type syslog set system host log-alias syslog endpoint 10.200.32.49:525 network tcp
supervisor@rtbrick: cfg> show config
{
"ietf-restconf:data": {
"rtbrick-config:system": {
"host": {
"log-alias": [
{
"name": "syslog",
"endpoint": [
{
"address": "10.200.32.49:525",
"type": "syslog",
"network": "tcp"
}
]
}
]
}
}
}
}
Example for Syslog configuration with UDP:
set system set system host set system host log-alias syslog set system host log-alias syslog endpoint 10.200.32.49:525 set system host log-alias syslog endpoint 10.200.32.49:525 type syslog set system host log-alias syslog endpoint 10.200.32.49:525 network udp
supervisor@rtbrick: cfg> show config
{
"ietf-restconf:data": {
"rtbrick-config:system": {
"host": {
"log-alias": [
{
"name": "syslog",
"endpoint": [
{
"address": "10.200.32.49:525",
"type": "syslog",
"network": "udp"
}
]
}
]
}
}
}
}
Displaying Logs for the Executed CLI Commands
The log group 'cli-execution' has been added under the rtbrick-cli module to provide information about the executed CLI commands. When this log group is enabled, all CLI command executions are logged and can be viewed using the show log command. This functionality enables operators to view CLI activity and configuration changes. It allows filtering CLI-related logs separately from other log groups.
Syntax:
set log module rtbrick-cli group cli-execution level info
Example command:
set log module rtbrick-cli group cli-execution level info
Example command:
set log module rtbrick-cli group cli-execution level info commit set system set system host set system host element-name ufi10.q2c.u9.r4.nbg.rtbrick.net set system host pod-name nbg4 set interface ifp-0/1/19 set interface ifp-0/1/19 forward-error-correction none set interface ifp-0/1/20 set interface ifp-0/1/20 forward-error-correction none set interface ifp-0/1/28 set interface ifp-0/1/28 forward-error-correction none commit
Example Output:
supervisor@rtbrick.net: cfg> show log [ Notice ] <2025-05-30T08:41:52.254661+0000> Launch service rtbrick-fibd, PID 314 [ Notice ] <2025-05-30T08:41:52.662366+0000> Launch service rtbrick-ifmd, PID 331 [ Notice ] <2025-05-30T08:41:53.037937+0000> Launch service rtbrick-lldpd, PID 346 [ Notice ] <2025-05-30T08:41:53.411325+0000> Launch service rtbrick-mribd, PID 361 [ Notice ] <2025-05-30T08:41:53.786770+0000> Launch service rtbrick-ribd, PID 376 [ Notice ] <2025-05-30T08:41:54.153642+0000> Launch service rtbrick-staticd, PID 391 [ Info ] <2025-05-30T09:08:03.629055+0000> User 'supervisor' executed command 'commit' [ Info ] <2025-05-30T09:08:10.188181+0000> User 'supervisor' executed command 'set system' [ Info ] <2025-05-30T09:08:10.196724+0000> User 'supervisor' executed command 'set system host' [ Info ] <2025-05-30T09:08:10.206858+0000> User 'supervisor' executed command 'set system host element-name ufi10.q2c.u9.r4.nbg.rtbrick.net' [ Info ] <2025-05-30T09:08:10.216635+0000> User 'supervisor' executed command 'set system host pod-name nbg4' [ Info ] <2025-05-30T09:08:10.290811+0000> User 'supervisor' executed command 'set interface ifp-0/1/19' [ Info ] <2025-05-30T09:08:10.307542+0000> User 'supervisor' executed command 'set interface ifp-0/1/19 forward-error-correction none' [ Info ] <2025-05-30T09:08:10.327628+0000> User 'supervisor' executed command 'set interface ifp-0/1/20' [ Info ] <2025-05-30T09:08:10.347832+0000> User 'supervisor' executed command 'set interface ifp-0/1/20 forward-error-correction none' [ Info ] <2025-05-30T09:08:10.368051+0000> User 'supervisor' executed command 'set interface ifp-0/1/28' [ Info ] <2025-05-30T09:08:10.553653+0000> User 'supervisor' executed command 'set interface ifp-0/1/28 forward-error-correction none' [ Info ] <2025-05-30T09:08:12.024264+0000> User 'supervisor' executed command 'commit'